

 |
 |
ICC Meeting: |
IFAS COMPUTER COORDINATORS
|
|
"Mobile computing devices purchased with University of Florida funds, including, but not limited to contracts, grants, and gifts, must also be recorded in the unit’s information assets inventory." There is a tooltip on the term "Mobile computing devices" in the above policy section that reads: "Small devices intended primarily for the access to or processing of data, which can be easily carried by a single person and provide persistent storage. New products with these characteristics appear frequently. Current examples include, but are not limited to, the following types of products: Laptop, notebook, netbook and similar portable personal computers; Smartphones and PDAs (Android, Blackberry, iPhone, and others)." |
Many of us are not in charge of inventory for our units; Winnie Lante, however, is one notable exception. Steve asked her via e-mail how this aspect is handled and she responded:
|
In the old system you listed it as an "Attractive Asset" and there was a totally separate place to add the item and request a decal. Now you just log into AM and go to "My Inventory" and hit "add item". It allows you to add the UFID number of the faculty member in charge of it, a full description and there is even a notes field that I use to add the name of the grad student if the item has been allocated for one. You need to add the purchase price, at least a close approximation, so that it still comes up as an attractive item and not a regular asset. They send you an Asset Tag. It's not too big a bother but I sometimes have problems getting them to bring the laptop to me for the tag install. I'm starting to think I should hold the device hostage until I can apply the tag. Problem there is that sometimes it takes weeks to get the tags. |
Steve noted that the person in charge of inventory for his unit was unaware of this requirement. Avi said that the Standard is not specific on how asset management must be handled, but this method would seem to be one good option.
Winnie said the real problem is knowing when an item that must be tracked is purchased. Avi said that he is working Asset Management currently to see if there is some way to improve that process.
Steve mentioned that asset tags were part of this and Winnie said that the default setting when an item is entered is to print a tag and send it to you. There have been problems in the past where Winnie had submitted items multiple times and still not received a tag, but she believes those issues have been worked out now. While you can uncheck that box, Winnie thinks the tags help the end-users realize that the device is valuable and needs tracking.
Winnie also mentioned that they have finally added a "notes field" where one can enter extra information on an item. She uses this to help discriminate exactly who might have been assigned that object (say a graduate student for example); otherwise items would only be traceable to the owner (Professor generally); she has faculty with large numbers of laptops, and this feature is really helping her keep track of who is responsible for each.
Winnie said that the web interface doesn't work very well in IE and she recommends either Firefox or Chrome.
Steve said that it would be good for the IT support in each unit to communicate all these details to the person handling inventory; it is unlikely that they will become aware of this requirement on their own. Winnie added that she is willing to help should anyone have any problems or questions.
Questions from the ICC
Q from Steve Lasley: How/when can we get detailed recommendations on encrypting external HDDs?
A: Steve noted that Wendy Williams had contact Avi individually on this aspect and Avi's emailed response to Wendy was as follows:
|
[...] As I said, there aren't good options for encryption of external hard drives. If it is doable in a particular situation, the best solution would be PGP. That way you get reporting, key recovery and cross-platform capability. The downside is that PGP has to be installed on every computer that will use the external drive. I have tested using Apple FileVault2 for external drives, and that works well. I have not personally tested Bitlocker, but would think it should work. I haven't checked, is Bitlocker To Go still supported? PGP used to offer a version call PGP Portable that had similar capability to Bitlocker To Go, but with the usual PGP server-side benefits, but I understand that has been discontinued. I have tested some older models of hardware encrypted external drives, including some with fingerprint authentication, but I'm not sure those are available any more. I asked one of our vendors to look into options like this for me, and he didn't turn up any current products. [...] please get back to me if you have any further questions. This may be a good topic for discussion on the IT-Discussion-L list, to see if anyone else has discovered any good solutions. |
Avi believes PGP is likely the best solution because it provides reporting, key escrow, and key recovery. The drawback is that to read such an encrypted device you must first install PGP Desktop on whatever computer you are accessing it from. Steve pointed out that this does not mean each computer must be encrypted with PGP, but rather that the PGP program must be installed and available.
It is difficult to find hardware encrypted external drives currently. Avi mentioned Ironkey as being one potential option. Steve asked about software solutions that are offered with some products. Avi said that such things sometimes weren't really encryption at all--it would just depend on the product. [In looking after the meeting Steve did note that Buffalo DriveStation Axis Velocity external drives appear to have hardware encryption and are available from CDWG (albeit at a price premium over non-encrypted drives).]
Q from Russell Hunter: "Why haven't the Security folks come out with one standard for encryption across the University for just this purpose? If we were all using the same product then I feel a lot of these issues would be self-resolved."
A: Avi reiterated what was said at the last meeting, namely that they were careful not to mandate a particular solution (since UF is very diverse) but were careful to provide a solution (PGP) should one wish to use it.
Q from Steve Lasley: How concerned should we be when we come across an unencrypted device? It is difficult to know where we should place such things in the hierarchy of all the things we have to do.
A: Avi suggested that we definitely put a high priority on any devices which you know are being used to store restricted data. Beyond such a situation, Avi would suggest working on this as time permits.
Steve mentioned that he will be talking with his faculty at their next meeting with the intention of making them aware of student data (since FERPA is what most affects us here in IFAS) and the need to keep that safely on the file server in their personal share. Such data need not be placed on portable devices at all and Steve feels that keeping folks aware of that should help considerably.
Password management needs to be a consideration as well in Steve's opinion; depending on the means used, a lost password could mean lost data. Avi asked if we are still seeing people using flash drives as he was under the impression that their usage was waning. The ICC seemed to agree that these are still very prevalent.
Q from Francis Ferguson: I had a user with a new Samsung tablet that gave a lot of pushback when I told them the device needed to be encrypted. How do we handle such situations?
A: Steve asked if she we using the device with UF Exchange and Francis said that she was. Steve noted that he uses Touchdown with his Android phone and that ActiveSync enforced a PIN on Touchdown but not on the entire device--though Touchdown apparently encrypts its cache. That might explain how she could be using Exchange w/o there being a PIN on the device itself.
Dan Cromer repeated that he does not see us as "police"; we can inform folks of what should be done and assist them with doing it, but that is as far as we need go. The responsibility ultimately lies with the individual as the university has absolved itself from responsibility; if people do not comply with the policy then UF will not back them--and they need to know that.
Q from Dennis Brown: What exactly is considered an "incident"? Is a lost device an incident or does something have to happen with the lost data itself?
A: Avi responded that a lost device was an incident. Once a device is lost we don't always know what happens to the information it contains; the Privacy Office normally assumes that such information was accessed. If the device is encrypted then there is no way the information can be accessed.
Q from Lance Cozart: We continually get vulnerability notices for Telnet on our AV devices. Some of these devices (e.g. AVer) have no means to turn off that protocol, and the management system used by VCS uses that protocol as well. How can this best be managed?
A: First off, Steve would like to note that this is an issue with more than just Telnet as Web/FTP/SNMP are protocols often used for AV device management as well. Steve also noted that we have had compromises on such devices in the recent past. Steve has suggested to both Patrick Pettus and James Moore that they investigate placing ACLs on the ports so that access to endpoints via Telnet was limited to only a set number of IP addresses as needed for management. Steve did not hear back, however. It seems to Steve that some coordination is required between VCS, security, and CNS network services to come to a suitable solution. There is no formal means for coordinating such efforts, however, which would require something of a "case manager" that could coordinate among the various groups until a solution was implemented.
Avi wasn't familiar with this particular Telnet vulnerability, but he did know that video conference devices are a bigger security issue than many might realize (see Board Room Spying for Fun and Profit). Avi said that the need for Telnet scared him a bit, but if that was indeed necessary then ACLs could be the solution; Avi suggested that the security office might be able to help with getting something implemented and he said that he would try to check into the issue further for us.
Dan Cromer suggested that UF might consider blocking port 23 at the DMZ as a potential mitigation. Avi responded that in the past the security office has lacked a framework that provided them the authority to firewall things (with few exceptions). Avi said he is working currently on a remote access policy, however, that will provide a framework and process to do this. Once that policy is implemented then UF should have a comprehensive method for looking at boundary security.
Q from Jimmy Anuszewski: There is a FAQ sheet that lists all the various anti-viruses for the Macintosh which are acceptable to the SafeConnect posture assessment software, but the first page suggests and provides access to installing Avast. Jimmy prefers that his users install ClamXav because it is the only product not requiring root access and has worked well for him. Jimmy would like to have an installation of that available up-front as well; otherwise people wanting to use that must first install Avast to even get network access so they can download ClamXav--a catch 22 of sorts. Is that a possibility?
A: Avi responded that he believed Avast was picked for recommendation based on the experience of the UF Computing Help Desk; Avast was the one that people had the least problems with. Avi also mentioned that the app store version of ClamXav is not compatible with SafeConnect. Jimmy did mention the need to activate the ClamXav Sentry module that does on-access scanning; that is necessary for SafeConnect compliance and is the module missing from the app store version. Avi said that he understood Jimmy's reasoning behind wanting to recommend ClamXav and didn't really have a good answer for that other than what he had already said.
Jimmy explained his frustration over having to uninstall Avast that folks have installed at the recommendation of the wireless instructions and then move them over to ClamXav. He would like to know what problems the Help Desk had seen with ClamXav as it has been trouble-free in his experience--including any mention of issues in the various forums which he frequents.
Dan Cromer said that we can still have ClamXav as an IFAS recommendation: first connect via wired Ethernet then download and install ClamXav prior to setting up UF wireless.
Avi noted that there seems to be some concern with helping faculty understand what they need to know regarding security. If we need someone to give a presentation for our unit, please let him know and he would be glad to arrange that.
Patching updates... (previous discussion)
Microsoft
The August Microsoft patches are expected to include 8 bulletins (3 "Critical", and 5 "Important") covering at least 23 CVEs in the usual suspects. A risk assessment should eventually become available here.
McAfee generally provides podcasts on the highlights of each month's offerings.
Since we didn't have time to talk about it last month, Steve would like to mention that the Enhanced Mitigation Experience Toolkit 4.0 is now available. IFAS may wish to consider deploying this via GPO as a means to mitigate vulnerability exploits.
Adobe
New security updates of Flash, Shockwave, and Cold Fusion were released on the second Tuesday of July. There will be more this month as well no doubt.
Also, apparently Adobe Reader 11.0.03 installs multiple vulnerable components.
Java
The next scheduled update will be in October, but who knows?
Apple
Jimmy mentioned seeing a question on the CCC list about how to handle iTunes app installs and upgrades. These require an account which in turn requires an associated credit card. Should we run into a user that does not have an account Jimmy noted that the most frequent updates are free Java or OSX and he just updates those for folks using his own iTunes credentials. Avi noted that there is a way to create an iTunes account w/o a credit card.
[In order to make meeting participation more efficient for Patrick Pettus and James Moore, these two topics have been moved to reside at the top of our agendas.]
Videoconferencing topics (previous discussion)
Endpoint security concerns (previous discussion)
See security discussion above...
Dan Cromer noted that the bridge, our Polycom endpoints, and Blue Jeans all support AES encryption of a videoconference. If a VC involves student FERPA data (Faculty to student academic discussions for example) then it really should be encrypted. Dan mentioned that the lack of encryption capability was why UFHealth would not approved Skype as a communications mechanism.
Replacing Polycom endpoints with some Lync-based solution (previous discussion)
Updates not available...
Possible end-point refresh in the works (previous discussion)
Lance Cozart was able to negotiate a price of $714.29 for the new AVer EVC100, which includes $13.87 shipping. In quantity 15+ the shipping will be free. This model was discussed back in June.
Lance has been establishing good price points on a lot of AV equipment; if you are looking at getting something it would be useful to contact him first. As one example, Lance has arranged for us to get Visix digital signage direct from Visix at cost. He has also qualified IFAS for a good deal of free AV equipment and is looking for a location that might make use of it.
Movi/Jabber Updates (previous discussion)
Updates not available...
Other standing VC topics
End-user Scheduling (previous discussion)
Steve noted that as of July 30th, only about eight OUs had populated their respective VCschedule notification lists: CREC, ENTNEM, FSHN, GCREC, IMOK, IRREC, SFRC, and WFREC. He would like to remind people that these lists are very useful as they control who gets an email notice when an endpoint is configured for connection via the bridge. The sooner we get these group populated, the sooner we can make sure all our endpoints are properly configured in TMS.
If you are concerned about the number of messages you might get, it is easy to create a rule to move them to a new folder via Outlook
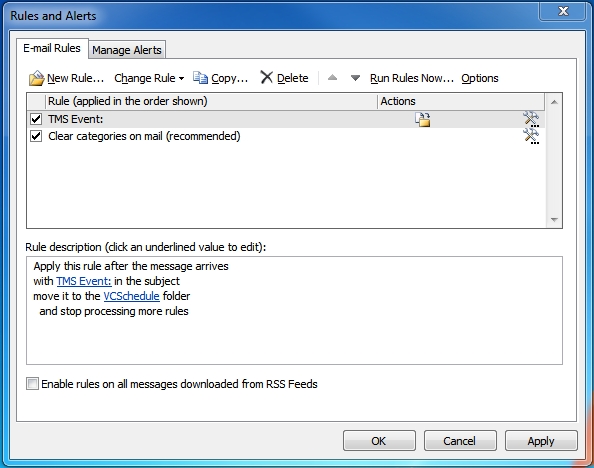
If you then add that folder as a favorite it is easy to see when new messages arrive as well, but without them cluttering your Inbox:
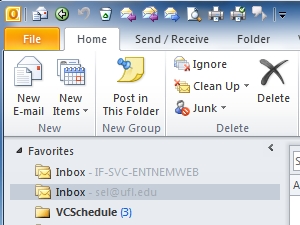
Yesterday Dean Delker sent out the following pertinent to these new changes:
|
Message from Dean Delker: You have probably noticed a lot of testing and changes in video conferencing services lately and have a lot of questions. I’m going to try to clarify some things in a minute, but before that Patrick asked me to find out how many ICC’ers might interested in being trained to use our Cisco TMS (Telepresence Manage Suite) fully-featured interface to create and edit video conferences? As it stands our new TMS “Smart Scheduler” will allow any user to create basic, simple video conferences and get a Conference ID Number back via email, but there are some glaring limitations. The only way around those are using the fully-featured TMS Scheduler. We are working on some training videos for that, and Patrick wants to institute a regular, probably monthly video conference for interested people just about video conferencing at VCS where you can get your questions answered, and we can get our information out. We’ll want to do the first one before the semester starts, so sometime next week, TBD. I’ll let you know. Meanwhile if you know you want to be a “Power Scheduler” you can email me at rdd@ufl.edu & I’ll compile a list for Patrick. In addition here’s the skinny on the “Smart Scheduler” although it’s name is debatable :-). I usually call it the “Simple Scheduler”, and it’s great for creating a basic video conference even on short notice especially when most or even all endpoints are going to join themselves via ConfID#. If you haven’t played with it yet on our website at https://video.ufl.edu/ Click on “Schedule a videoconference” under “Quick Links” Here you’ll find some training videos or you can continue to the “Smart Scheduler” and click on it. The next page will list future meetings you are owner of and could modify and let you create new ones. The SS only works with endpoints which stay turned on and TMS can manage which Cisco calls “Telepresence Rooms”. That means they have to have an interface that interacts with TMS, we know the admin password, etc. Most Polycoms can do that if they are still on maintenance contract. We can use TMS to keep them upgraded and working right. Older models might not qualify. And some newer, low cost video conferencing brands like AVer or LifeSize might not be fully featured enough to be sensed by TMS. So you are limited to either Telepresence endpoints or dial-ins. In addition TMS can’t manage endpoints behind firewalling like with County Extension where county IT controls things. Also you can’t create recurring meetings, can’t schedule endpoints just by IP address, and you have to build in your own beginning & ending buffer times. And presently if you wanted the bridge to call out to sites automatically which weren’t qualified Telepresence sites that would involve the fully-featured TMS Scheduler which means you’ll want to use the traditional request program and VCS would have to create the event for you on the bridge. On our home page click on the orange “Request Service” box in the upper right quadrant and click on the “Facilitated Videoconference” radio button. I’ve been told there are future plans to charge for that, but till we can train some “Power Schedulers” that link will take you to the traditional request program, and we’ll create it for you as before making you the owner. Or theoretically people could create an event with the Simple Scheduler and email video@ufl.edu with custom additions they might need. |
Lync updates (previous discussion)
Updates not available...
SIP may replace H.323 as preferred protocol for endpoints (previous discussion)
As Dan Cromer explained (and was mentioned in last month's notes), the industry is moving to all SIP.
Blue Jeans (previous discussion)
Dennis Brown asked if people were using Blue Jeans; he was a bit confused over the multiple solutions available.
Dan Cromer had shared with Steve a couple of Blue Jeans features which he learned of recently. First of all, each Blue Jeans account has a personal meeting ID associated with it that is automatically set to a unique 10 digit number. This can be changed to another number after logging in, however, by clicking on the personal meeting, then "Edit Personal Meeting", then Advanced Meeting Options, then (View Configuration) in small letters at the bottom, then click on the Pencil icon at the right of Personal Meeting ID:.
Dan and Steve have changed their meeting IDs to their phone number. This makes it easy for folks to know how to access a personal meeting for someone and these are a great way to handle ad hoc meetings rather than having to schedule meetings.
The above feature gave Dan the idea of creating a Blue Jeans account specifically for the ICC, with a personal meeting ID of "7890123". In the future we will use this for our ICC monthly meetings or for any other ad hoc meetings that we might need. Those with Blue Jeans accounts may login via http://ufl.bluejeans.com.
Dan also mentioned that Blue Jeans now supports video uploads which can then be played within a meeting. Steve tasked Jimmy with locating a short humorous video for each meeting (should he decide to accept the challenge).
Dan reminded us that there is a Polycom app for Android and iOS as mentioned at our May meeting.
WAN (previous discussion)
Updates from James Moore
Updates not available...
Wireless printers (previous discussion)
We had talked last meeting about the need to connect wireless printers to UF wireless. Jimmy Anuszewski said this is quite a problem for him because folks have bought wireless printers on their own expecting them to work, and he has to be the one to tell him that they won't--at least currently. Dan Cromer said that this is being worked on. Avi said that this is something that is actually being addressed as part of the PrintSmart initiative as most models have a wireless option. Avi did not know the timeframe on that however. Part of the problem is that the UF network does 802.1X WPA2 Enterprise EAP authentication. This utilizes user credentials and raises the question of how is the printer going to login.
Steve noted that someone came to him the other day wanting to connect a Canon EOS camera to wireless. Even more concerning was the software they said made it easy to wirelessly move files from the camera to the desktop. Steve assumes this makes the computer a server of some sort (likely FTP) and he surely doesn't what new server ports popping up all over the place.
Steve asked Kevin Hill if Nancy Watson had deployed Flex Connect on the new WAPs at Immokalee yet (as mentioned in last month's meeting notes). Kevin responded that she is doing a test first with P.K. Yonge here in Gainesville. Flex Connect apparently permits switching client data traffic locally as well as performing client authentication locally; this would address Kevin's concern about all local WAP traffic having to route back through Gainesville. Kevin said he would know a little more next week once they get a test AP set up. Kevin mentioned that there are other alternatives should Flex Connect prove not to be a suitable solution for RECs or CEOs; we could perform our own 802.1x health assessment using the MPS servers and Microsoft NAP.
Steve said that Matt Grover is looking into creating a private WLAN for wireless printers that could solve our current authentication problems with wireless printers on UF wireless.
VoIP at RECs
Updates not available...
Phone bills to be paid for centrally? (previous discussion)
Updates not available...
UFIT/CNS discontinuing UF Jabber and UF Usenet services
This was announced on July 23rd:
|
Message from UFIT/ CNS: As of December 15th, 2013, UFIT/CNS will be discontinuing the UF Jabber and UF Usenet services (jabber.ufl.edu and usenet.ufl.edu). Retiring these services will allow UFIT to focus more on delivering higher quality, more robust enterprise messaging solutions that we already have in place. Users who need Jabber-like functionality should seek an alternative such as UF's Lync service: http://www.mail.ufl.edu/About%20Lync.shtml Users who need Usenet-like functionality should seek one of the many alternative NNTP offerings provided by various Internet service providers. If you have any questions about this process, or need additional assistance migrating to Lync, please contact the UF Computing Help Desk: UF Computing Help Desk |
Notes from July SIAC meeting
Steve had hoped that the notes from the July SIAC meeting would be available by now, but that did not prove to be the case.
July's IT Directors Meeting Notes
Steve asked about what had transpired at the July Campus IT Directors meeting. Dan said that he didn't go to that meeting but that he would get the notes for us. Wendy Williams had joined the meeting early-on but was not available to comment once we got to this section.
Steve appreciates Dan getting us those notes because we learned last meeting how important feedback via that committee is to IT governance. We certainly can't provide any useful input if we aren't kept up-to-date in a timely fashion.
Note: Dan made the notes available on August 13 here on SharePoint.
UF Authentication Management Policy and Standard and Password Complexity Standard (previous discussion)
The official notice of implementation was distributed on Monday, July 15th. The Authentication Management Policy along with the related Authentication Management Standard and Password Complexity Standard are now available on-line.
PrintSmart initiative (previous discussion)
See wireless printing discussion above.
Avi wanted to remind people that as we start to replace printers/copiers under this new program that we need to attend to the proper disposal of data on our previous machines. The Security Office is working with Asset Management and Purchasing to get some good procedures in place for that, but with departmental equipment especially this is still up to local IT support to address.
New IT Service Management Initiative
There was a "ITSM 101: What Every IT Professional Should Know" presentation on July 9th; the recording and PowerPoints are available here.
Steve noted that "PR" notices continue to come out including the following from Tracy Gale yesterday:
|
The new IT Service Management (ITSM) initiative is being developed to increase the efficiency and consistency of services provided to faculty, students, staff and the greater UF community. If you work directly with customers, ITSM will mean:
If you help manage operations, ITSM will mean:
If you provide Tier 2 or Tier 3 technical support, ITSM will mean:
If you are involved with IT projects, infrastructure, and programming, ITSM will mean:
If you manage IT staff, ITSM will mean:
If you submit requests for assistance from IT colleagues, ITSM will mean:
If you have questions or would like more information about ITSM, please e-mail ufit-itsm@ufl.edu. A communications archive, including the video stream link to ITSM 101 and all news stories and major email announcements, is online. |
Steve noted that these raise more questions for him but are certainly raising expectations as well; hope springs eternal. Steve asked about the Tier and Dan Cromer responded that Tier 1 refers to the Help Desk, Tier 2 is local unit IT support, and Tier 3 refers to the service providers/managers (like Exchange, SharePoint, etc.). We obviously don't want faculty talking directly to Tier 3.
Dan and Avi both noted that these changes mostly involve improving/fixing Remedy.
Content Management System (CMS) for UF: Entering purchasing phase (previous discussion)
Jimmy said that UF has picked TerminalFour, but both he and Dan Cromer said that implementation will take quite some time. Dan said that the next step will be for this to go to the UF IT Policy Council. This project has to be funded and Dan expects that funding will be put off a year so that this can be rolled into the upcoming 5-year RCM review. This is the same delay that happened to the proposal for having the $11/mo. phone charges being paid off-top centrally.
Steve said that one of his users had mentioned hearing that IFAS is moving everything to WordPress. Steve has always tried to dissuaded folks from WordPress both because Santos has grave support concerns on the server end (centered on MySQL backup methods) and because we have over four dozen "sites" managed by nearly as many individuals that reside within sub-folders of our departmental site. Moving the main departmental pages, which are at the root, to WordPress would mean moving everything as far as Steve knows; coordinating that would be a nightmare.
Dan Cromer said that he strongly discourages WordPress as well; adding that the security and authentication model of WordPress is problematic. Dan recommended referring folks that ask about WordPress to Tennille Herron, the IFAS web master; she will tell them no as well.
Authentication Management policy draft (previous discussion)
Updates not available...
New 'Trouble-Ticket' Entry Page for CNS (previous discussion)
Updates not available...
KACE (previous discussion)
Dan mentioned that he is continuing to post reports each month and he was wondering if anyone looks at those or not. Steve said that he hadn't but several others mentioned that they do look on occasion. Dan wanted to ask because he knows that Windows XP end-of-life is looming for us April 8th, 2004. Most of us are aware of the problem and have let our users know. A number of Windows XP machines are going to continue in use due to being used with special software/equipment, but they will just have to be used off-network after next April.
CNS working to implement NAC for UF wireless (previous discussion)
Updates not available...
UF Exchange updates (previous discussion)
Outsourcing of student e-mail?
Updates not available...
Outlook asking for re-authentication
These problems continue. Steve noted that he still seems to have to use a VPN in order to connect from home but once he does connect then the VPN no longer seems to be necessary. Dan said that the VPN isn't really necessary but does speed up the initial connection, which can take up to three minutes or longer. This situation that first began after the F5 installation continues to be very annoying for all.
Sakai e-Learning System now in production (previous discussion)
Updates not available...
Alternate IFAS domains in e-mail (previous discussion)
Updates not available...
Split DNS solution for UFAD problems (previous discussion)
Updates not available...
New web cluster (previous discussion)
Updates not available...
Windows 8 Deployment? (previous discussion)
Updates not available...
SCCM for IFAS
Work continues on the central SCCM plans.
Updates not available...
Exit processes, NMB and permission removal (previous discussion)
Updates not available...
Services Documentation: Is a Wiki the way? (previous discussion)
Updates not available...
Moving from McAfee VirusScan to Microsoft Forefront Endpoint Protection?
Updates not available...
Print server (previous discussion)
Updates not available...
Recording lectures for Distance Education (previous discussion)
Updates not available...
New DHCP reservation site created (previous discussion)
You are reminded that Santos Soler has created a new DHCP reservation site which you may use to request reservations.
Restoration of back-ups on the file server
Wayne Hyde intends to document and announce proper usage as time permits.
Membership of ". IFAS-ICC" e-mail distribution group to be narrowed to ICC members only (previous discussion)
Steve will keep this as a standing item on our agendas for now as a reminder. The ICC distribution list is more targeted and restricted to IFAS IT support folks only.
IFAS efforts toward Green IT (previous discussion)
Steve asked if this can be removed from our agendas and Dan Cromer said that the topic remains but has been pushed way back in priority due to other more pressing concerns. Dan did note that the standard Dell system now comes with a low energy power supply. The other issue remaining involves wake-on-LAN which is awaiting funding; this may get evaluated for inclusion into RCM next year as well.
Creating guest GatorLink accounts: singly or in bulk (previous discussion)
Steve had left this on the agenda in case further discussion was deemed warranted.
DirectAccess pilot (previous discussion)
Dan Cromer said that CNS feels they do not have the resources to implement DirectAccess. Consequently, a consortium of UF departments has organized to move forward with this. Wayne Hyde is now the leader of that with Keith Baker of CLAS IT and a couple of others. Steve was very pleased to hear this as he believes it will help our users tremendously as well as relieve a considerable support burden for our local IT support staff.
VDI desktops as admin workstations (previous discussion)
Updates not available...
Wayne's Power Tools (previous discussion)
Updates not available...
Computer compliance tool update (previous discussion)
Updates not available...
Folder permissioning on the IFAS file server (previous discussion)
You are reminded to please take the time to read and implement the new standards. If you have any questions get with Wayne or Steve.
Disabling/deleting computer accounts based on computer password age (previous discussion)
This is yet another matter for which finding time for implementation is proving difficult. Steve wants folks to remember that Andrew Carey had a good plan for dealing with this which perhaps Alex York's replacement can find the time to address eventually. In the meantime, it would be very good of each OU Admin to consider mimicking the proposed plan manually by keeping their own records and deleting any computer object which have been disabled for 90 or more days; Wayne's Power Tools can identify those. Steve has finally begun doing that for his own unit and it has made his view within ADUC much more agreeable.
Since BitLocker stores its keys within the computer object in UFAD, Chris Leopold was considering scavenging those keys for secure storage elsewhere. That would provide a fallback for decrypting a drive should the associated computer object be deleted.
Core Services status (previous discussion)
Updates not available...
ePO updates (previous discussion)
McAfee announced EOL for the Daily Engine and DAT SuperDAT package as of July 24th.
Wayne had reported the following on Monday:
|
Message from Wayne Hyde: For those of you using ePO 4 to upgrade client machines to VSE8.8i, please tag your systems with “Push88” or “PushAV” (or both). There was a problem with the tag processing task where systems with 8.7i may not upgrade to 8.8i even if tagged with “PushAV” as the tag could get cleared before the client attempted an upgrade. The glitch should be fixed now. |
Wayne said that some issues remain with ePO5, including some bugs in the 4.8 agent. He added that Alex leaving has left ITSA rather short-handed as well.
Status of SharePoint services (previous discussion)
IFAS migrating to centralized MOSS
Updates not available...
Public folder file deletion policies and procedures status (previous discussion)
Updates not available...
MS Office News update (previous discussion)
Office 2010 SP2 became available on July 23rd; it is being offered via Microsoft Update currently. The details and the download are available from Microsoft. Steve has updated the IFAS 32-bit install site already.
Some have started to install Office 2013 apparently, but Steve is still holding off due to reports of various unresolved issues--including those with Lync such as it not being able to connect to the VC bridge. Wayne noted that the default offline cache options in Outlook are set to one year (see KB2733062); you must go into the configuration and tell it to keep all your mail offline if you want to locate older emails via search. Chris Leopold ran into that and Wayne is going to stay with Office 2010 until he stops hearing Chris cry at the end of the hall.
Dan did note that if a user having Office 2013 runs into the "Lync won't connect to VC bridge" issue that installing Jabber makes much more sense than installing Lync 2010 (which can co-exist with Lync 2013). Jabber is a much superior client for bridged videoconferences in any case.
Job Matrix Update status (previous discussion)
Updates not available...
IFAS Directory update
Xin recently updated the IFAS Directory site:
|
Map of IFAS Sites:
Advanced Search (Email to selected employees in a unit)
|
Dan had Steve pull up the new map. In doing so, we noticed a considerable delay in updating the map when various options were selected. In fact, some options didn't seem to appear until yet another option was selected (on IE); this made the interface a bit confusing.
Dan wasn't clear on whether or not the new IT employees page was dynamically generated. He did know that there is a check box where a liaison marks an individual as being the unit head and in the department lists (advanced search) this is used to sort those to the top. Winnie noted that the list for her department incorrectly sorted someone else to the top for SFCR; this turned out to be an error in the data which her departmental liaison has since corrected. There is an option to email these lists but it did not seem to work for Steve in the meeting (or later at his office) for some reason. Dan mentioned that this would have been an alternative way to address Dr. Payne's email frustrations (see following) as well.
Dan noted that they are working on pulling employee data from PeopleSoft so that it was populated in an official way. There, of course, is additional information for individuals (specialty, nickname, etc.) that would still rely upon directory liaisons for updating as well, but it would definitely improve the situation overall as listings will be pulled when folks leave and liaisons could be informed automatically when new records were added for their unit.
VP communication frustration (previous discussion)
After some confusion as to how much discussion Dan Cromer sought on the issue, he sent the following to us back in mid-July:
|
Message from : All, I discussed the distribution lists request with Dr. Payne, and he agreed that there was no need for a separate list for staff only, so we just need lists for faculty and all. At this point, after much consideration and input, here are my conclusions:
Note that it has been my desire for some time to update the IFAS Directory directly from other authoritative sources for core information rather than manually by Directory Liaisons, though some data elements, such as preferred name and specialties, would still need to be added by the Liaison. We are working internally to implement this process. Dan |
In order to assist those wishing to use option 1 above, Steve prepared Distribution Lists documentation in the secure portion of the ICC website (ufad\if-admn credentials required).
Dan Cromer noted that he really prefers Listserv because of its automatic archiving. Steve noted that the ICC distribution lists and ICC-L are both archived to a public folder currently (at: All Public Folders\IFAS\IFAS Computer Coordinators)--something that Dwight Jesseman had set up a long time ago. Steve's point was that archiving of distribution list is possible via public folders if that is deemed necessary.
Adobe licensing
Dennis Brown asked about the status of Adobe licensing. Dan Cromer replied that negotiations are in progress and he expects some new contract to be in effect before too very long. In the meantime, there is a new license for Foxit PhantomPDF available at very reasonable cost; unfortunately, this is Windows only. Nuance PDF Converter for Windows and the Mac is available but there is no UF license currently for that.
Dan Cromer mentioned his belief that Adobe Reader is superior to some of the other free PDF readers in that it will let you fill out and save forms. He also mentioned that Adobe Acrobat's particular signing function may require it to be used for some purposes.
Two-factor authentication
Avi said that this is being looked at as part of a Gatorlink Account Management Process project. They are unlike to go with biometrics, but rather will likely offer some one-time password scheme similar to Google Authenticator.
The meeting was adjourned just a trifle early at about 11:55 AM.