

 |
 |
ICC Home / Members / Meetings / Peer Support / Documentation / Projects
Blocking infected hosts:Return to IT/SA Services Documentation: Security Tools |
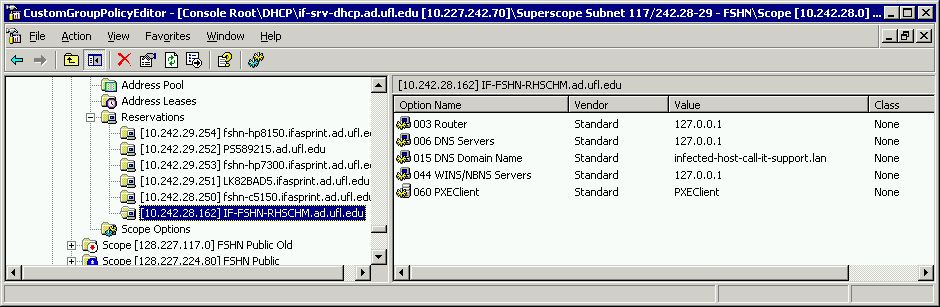
One of the quickest methods for limiting network access by an alleged infected host is to set a DHCP reservation (as opposed to addressing this at the switch or router level). Following is an example from a recent incident; it shows how the settings have been modified to deny egress. This configuration will cause the machine to use the loopback address for name resolution and routing. It will not prevent a machine from accessing the local subnet, however, so it is no substitute for unplugging. |
last edited 27 September 2006 by Steve Lasley