So, you got an email alerting you that computer objects within your OU are out of compliance...
Brief History:
ITSA has implemented an application that encourages users to report, or silently collects the computer objects that are out of compliance with current UF and/or IFAS policies. An additional server-side component notifies the local OU administrator, via email, of non-compliant machines found within their OU. It is this server-side component that is most likely responsible for you being directed to this URL location.
What does out of compliance mean?
IFAS has required policies that are outlined in “IFAS IMM 6C1-6.150-3”, http://imm.ifas.ufl.edu/6_150/6150-3.htm. UF policies are outlined at http://www.it.ufl.edu/policies/
Once the application finds an out of compliance machine, it will do one of two things depending on its run mode: Either it will notify the user via a windows popup message indicating that compliance issues were found with your system, or it will “silently” write a Comma-Separated Values (CSV) text file to a network location that contains information of what was found to be out of compliance.
Where can I find the text file that tells me what computer objects are out-of-compliance?
Non-compliant machines will have an associated log file (named “HOSTNAME.CSV”) located under a sub-directory that is named after the respective OU where the computer object was found. This log file contains the details of the out of compliance checks that is updated every time a user logons to the host.
This log file(s) can be found at the following location:
\\ad.ufl.edu\ifas\Out-of-Compliance
You will need to use your IF-ADMN-Gatorlink account to access this location (see below for instructions).
How do I access a file share with different credentials?
There are known issues with running Windows Explorer and Internet Explorer as a different user with certain Operating Systems. You can install something like xplorer2-Lite, http://www.zabkat.com/x2lite.htm (GUI-based file browser interface), use an elevated command prompt (runas /user:ufad\if-admn-gatorlink cmd.exe) or use an elevated notepad.exe (runas /user:ufad\if-admn-gatorlink notepad.exe)
Is there an alternative to accessing the file share?
Yes, there is a server-side component of the IPCC application that will notify the local OU administrator, via email, of non-compliant machines found within their OU. The OU admins should receive this notification every Tuesday @ 6am. If you are not receiving these notifications, please email help@ifas.ufl.edu to be added to the distribution list.
In addition, ITSA has created a website, http://icc.ifas.ufl.edu/ipcc/, that can be used to view the out of compliance systems.
I have fixed the issues with the host but it still shows it out of compliance, why?
Compliance status is updated only after the IPCC application runs. Once you have fixed the issues you have two options to update the host’s status:
- Have the user logoff and log back on to the system.
- Manually start the application by typing "\\ad.ufl.edu\netlogon\ifas\ipcc \\ad.ufl.edu\netlogon\ifas /s" at the command prompt of the machine in question.
It is noteworthy to mentioning that if you omit the "/S" option in the above command, the IPCC application will run immediately in interactive mode (no waiting on a timer). A popup window, instead of a .csv log file, will show any out-of-compliance results. If no popup window appears, the system is fully compliant.
What exactly is contained in the out-of-compliance log files?
The log files are formatted as CSV text files. They contain important information that will help you determine what is out-of-compliance with the host. Below is an excerpt from one such log file.
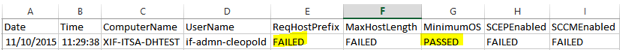
Each record is on a single row (created when a user logs into a non-compliant host)
Each column (A-H) represents a specific field that is separated be a comma
Each value is a simple “PASSED” or “FAILED”
Required Host Prefix:
IFAS computer names must start with "IF". This is because UFAD is a UF wide resource, and it is important to quickly identify the ownership of a computer object based on its name.
Solution:
IFAS has officially adopted the naming standard of “IF-OU-Something”. It is suggested that departments use this standard so that computer objects can be quickly identified as belonging to a specific IFAS department.
Maximum Host Length:
The NetBIOS naming convention allows for 16 characters in a NetBIOS name. Microsoft, however, limits NetBIOS names to 15 characters and uses the 16th character as a NetBIOS suffix. Therefore, naming standard of “IF-OU-Something” must not exceed 15 characters.
Solution:
Rename the hostname to be 15 characters or less.
Minimum OS level:
The ICC has voted to adopt IFAS Minimum OS level for client machines as Windows 7 Service Pack 1.
Solution:
Upgrade the Operating System to Windows 7 Professional SP1 or higher.
SCEP Enabled:
System Center Endpoint Protection or Windows Defender is the current antivirus/antispyware product approved for use within IFAS.
Solution:
By default Windows 7 or higher will enable Defender. However, it is suggested that you install the System Center Configuration Manger agent on the client system to automatically push System Center Endpoint Protection. SCEP is superior in that it can be centrally managed whereas Defender cannot.
SCCM Enabled:
System Center Configuration Manager provides such services as remote control, patch management, software distribution, operating system deployment and hardware/software inventory. IFAS has a top level GPO that will install System Center Configuration Manager agent on all computer objects under the IFAS OU.
Solution:
You should email help@ifas.ufl.edu for assistance in resolving this issue.
McAfee Virusscan Disabled:
The UF agreement with McAfee has been terminated and no machine at UF should have this software running. There is a top level GPO that will install System Center Configuration Manager agent on all computer objects under the IFAS OU. That SCCM agent will install SCEP and that should remove the McAfee software.
Solution:
You should email help@ifas.ufl.edu for assistance in resolving this issue.
McAfee Framework Disabled:
The UF agreement with McAfee has been terminated and no machine at UF should have this software running. There is a top level GPO that will install System Center Configuration Manager agent on all computer objects under the IFAS OU. That SCCM agent will install SCEP and that should remove the McAfee software.
Solution:
You should email help@ifas.ufl.edu for assistance in resolving this issue.
Windows Update Service Enabled:
There are numerous startup states associated with any given process, Automatic (Delayed Start), Automatic, Manual and Disabled. However, there is one particular startup state that the Windows Update Service should never be in and that is in a Disabled state.
Solution:
Follow the steps outlined at http://computerstepbystep.com/windows_update_service.html or email help@ifas.ufl.edu for assistance in resolving this issue.
Background Intelligent Transfer Service Enabled:
There are numerous startup states associated with any given process, Automatic (Delayed Start), Automatic, Manual and Disabled. However, there is on particular startup state that the Background Intelligent Transfer Service should never be in and that is in a Disabled state.
Solution:
You should email help@ifas.ufl.edu for assistance in resolving this issue.
Required WSUS Server:
Windows Server Update Services enables IFAS to manage the distribution of updates and hotfixes released for Microsoft products to computers within our environment. This application verifies that the WSUS agent is properly installed and configured by checking the host for the existence of a specific Registry Path, Key and Value.
Registry Path: HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
Registry Key: WUServer
Registry Value: http://IF-SRVV-SCCM-C.ad.ufl.edu
Solution:
You should email help@ifas.ufl.edu for assistance in resolving this issue.
|



