

 |
 |
ICC Meeting: |
IFAS COMPUTER COORDINATORS
|
|
Message from James Moore: I am still playing catch up from being on leave. I will be in meetings with the John Madey and the VoIP team today discussing VoIP pricing for Apopka, Homestead, Quincy & Immokalee. Kevin Hill has the fiber install wrapped up in Immokalee. I finished negotiating vlans and the cross-connect yesterday. Router and FLR component in process. I am ready to pull the trigger on the Verizon 3G / 4G connection (2) for the Austin Carey Memorial Forest. I received the paper work last week. I will be in attendance at the next ICC meeting with a good summary update of where we are and a "what we have left type of rollup." |
Steve asked Allan Burrage how the Lake Alfred upgrade was progressing. Allan did not hear the question for some reason, but Andrew Carey was able to fill in a few of the details. Andrew said that a Configuration Manager server was configured there as of yesterday; that server is tied into the IFAS Primary Site here on campus as a Child Site. This will be used to deploy Windows 7 SP1 locally. Andrew also mentioned that he believed their phone conversion is nearing completion; this means they are basically "full steam ahead" on the Active Directory migration.
When asked about the ConfigMan configuration, Andrew said that they had made some decisions based on upcoming architectural changes in Configuration Manager 2010 (currently in Beta 2). Lake Alfred has a distribution point (basically a glorified file server and TFTP PXE boot server) that synchronizes with the on-campus distribution point. This will allow local machines to PXE boot to that server and pull down the same images available to the Help Desk here.
Steve said he had spoken with Allan about the plan for the phone system and it sounded like they would have the "best of both worlds". As Steve understood things, they would be tied into UF's system but would retain their local numbers (CNS/Telecom is picking up the cost of the PRIs) as well as their local Call Manager Express box. Calls back to campus will be routed over the data network, removing those long distance charges.
myUFL changes on May 10th: affects on end-users (previous discussion)
Steve mentioned that he had not had any end-user question/complaints about this transition and asked if any of the other ICCers had anything to report on that. Dennis Brown mentioned that he did have one person who appeared to have the correct roles for accessing the travel portion of that system, but was not receiving the desired menu option; Dennis planned on following up on that later today.
Nick Smith had tried to raise some interest via the ICC in meeting the new browser requirements (see specifics for IE7, IE8, Firefox, and Safari) via GPO settings. Steve was in favor of that being done for Co-Managed provided it was carefully tested prior; in general, however, Steve tends to let such things be driven by need. If the number of support calls warrant the time spent on that, then he would certainly move in that direction. Andrew had pointed out that much of the configuration has to be done through registry setting within Group Policy Preferences (GPP) as Policy Settings would wipe out all of the users' current settings or prevent them from making future changes and adding additional entries. Steve had learned this the hard way as documented previously.
Andrew summed up by saying these settings can certainly be controlled via the Co-Managed GPO if everyone agreed that should be done.
New Secunia site license (previous discussion)
Updates not available...
Free Windows 7 Deployment Training for UF IT Staff (previous discussion)
Steve noted that a number of ICCers participated in some or all of this including David Bauldree, Dennis Brown, Allan Burrage, Andrew Carey, Francis Ferguson, Chris Leopold, and himself. Steve found it very useful and it reinvigorated his interesting in learning more about the Microsoft Deployment Toolkit. In particular, Steve finally started going through his copy of Johan Arwidmarks and Mikael Nystrom's "Deployment Fundamentals, Vol. 1". This book fills in a lot of the questions raised by the training sessions (and raises many more as well).
Steve has decided to utilize two separate deployment shares. The first one will be used with VMWare Workstation to build fully patched images of Win7x86 and Win7x64; currently Steve has a "suspend task sequence" worked into the build which allows him to customize the desktop (add the Computer icon) and IE (Home page and default search engine). He plans to include Office in the default builds, but since he is not fully committed to Office 2010 yet, he plans to keep separate images with either the 2007 or 2010 version for now. That will work out to four reference images to maintain overall.
Using VMs for the reference builds is definitely the way to go. Snapshots really save time with this whole process as they allow reversion to the "suspended task sequence" state previous to the last sysprep. Basically, you just get that snapshot running, add in any updates, save a new snapshot and resume the task sequence which runs sysprep then captures the new reference image.
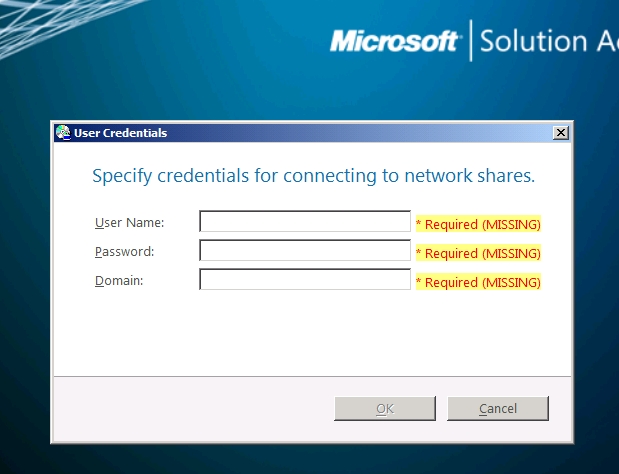
The production builds will use one of the four reference builds. A quick edit of the x86 or x64 task sequences can set which reference image to use. Drivers are handled by creating a make/model driver folder structure and using a DriverGroup filter so the proper drivers are injected (see video). Deployment begins via WinPE boot off a UFD on the target machine. Separate UFDs will be needed to kick off x86 or x64 deployments. For flexibility, (and since he has to visit the box anyway because he is not using WDS) Steve did not go with a completely quiet install. During the deployment one is currently prompted for:
Credentials for attaching to the Distribution Share
Task sequence selection (i.e., x86 or x64)
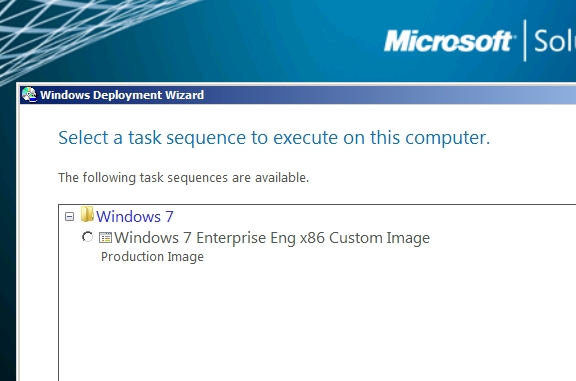
Steve's been working on x86 so far and only had that sequence available when the above screenshot was taken.
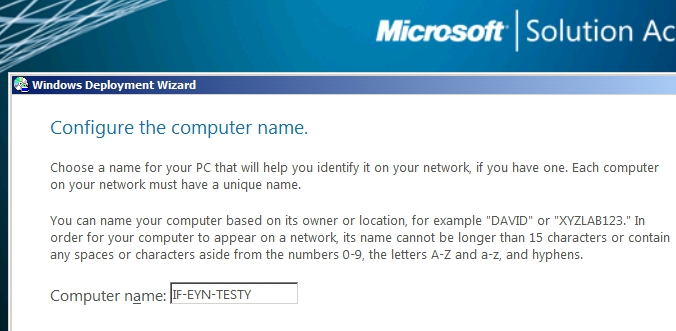
Machine name
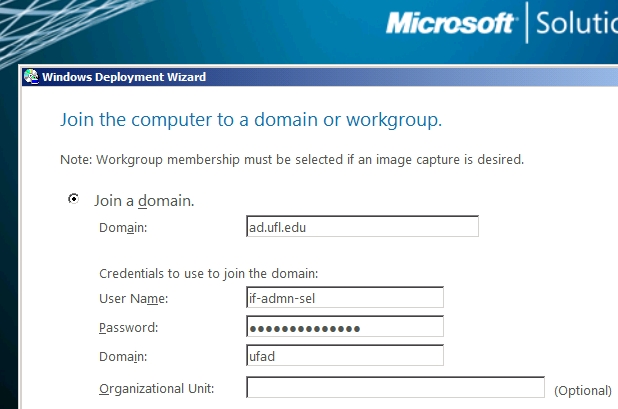
Domain join info (am prestaging currently to control OU location, though you can easily add a drop-down list box of OUs to pick from)
Applications to install
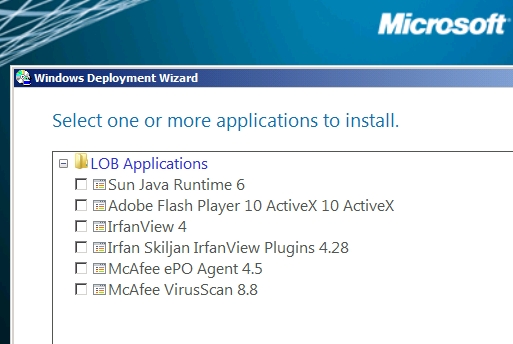
Once those initial details are handled, the remainder of the build proceeds automatically. Steve has only gone through the complete process on a single test machine so far and issues will no doubt arise, but he is very pleased with how this is working so far.
If this has piqued anyone's interest in MDT 2010, you might take a look at this Introduction to MDT 2010 Lite Touch video to get the basic idea. Steve would be glad to help anyone who might have further questions as well.
Update on domain policy and redirect duration (previous discussion)
Steve mentioned that the next ITPAC meeting has been scheduled for June 7th. [Note: this was later changed to June 20th.] Steve had been hoping Wendy Williams would be available to comment as she was appointed to run a sub-committee looking into this matter.
Dan Cromer wants to get an ITPAC recommendation on restricting use of the IFAS VPN.
Dan also wants to propose to ITPAC that we amend the IMM regarding "Computer Security, Support, and Operating Environment" to specify that unsecured WiFi access is prohibited. Steve asked how the new wireless access policy mentioned at our January meeting played into this. Dan responded that such access was still secured via a password; this new policy would simply prohibit the usage of wide-open access. Dan said that this is actually in the UF Acceptable Use policy with the "Users must not attempt to implement their own network infrastructure" item, but he wants this explicitly stated again within our own policies.
CNS working to implement NAC for UF wireless
This was initially announced about two and one-half weeks ago.
|
Message from the UF IT Security Team to NET-MANAGERS-L: Please share this announcement with your users. Starting May 1, 2011, big changes are in store for the university’s wireless network! If your portable computer runs Microsoft Windows, it will need to clear a security check every seven days before it can connect to the UF wireless network. The security check will verify that your computer has current antivirus software and all Windows updates before you can use the UF wireless network. Securing your computer protects you from identity theft, damage to your computer and files and also helps prevent harm to the university network. If your Windows-based computer already has antivirus software and is set to install updates when Microsoft releases them, you will experience only about a 30 second delay when connecting to UF’s wireless network. If your computer passes the security checks, they will not run again for seven days. If the security check finds a problem with your computer, you will first have to install antivirus software or missing Windows updates before using the UF wireless network. Note: to run the security checks, your Windows-based computer must have Java or ActiveX installed and enabled. The security check process begins on May 1, 2011. During Summer A, your computer will be allowed to connect even if it fails the security checks. However, if your computer does not have either Java or ActiveX controls installed, the security checks cannot run and your computer will be unable to connect to the UF wireless network. Starting July 10, 2011, your computer will only connect to the UF wireless network if it passes security checks. The security checks impact only Windows-based computers, and only when they attempt to connect to the UF wireless network. Computers not running Windows, such as Apple MacBooks, are not affected. Mobile phones are also unaffected by these changes. This security check process is similar to checks performed on the Housing and Residence Education network and the Health Science Center network. To help set up your computer to pass the security checks, UF is providing a software application called CloudPath Xpress Connect that will configure your computer properly to run the security checks. If you run into problems, the UF Computing Help Desk is available to assist with the new wireless security check process. Call or email the Help Desk at (352)392-HELP (4357) or helpdesk@ufl.edu. For more information on compliance with the new wireless security check process, or with any of the university’s information security policies and initiatives, visit the Security Web site. If you have any questions about this email, please contact: UF IT Security Team |
It was noted via the ICC-L that IFAS facilities off main campus would be excluded from this new policy. Kathy Bergsma also responded quickly to the CCC-L with the Cloudpath link which had been inadvertently omitted. Then, two weeks ago, the plans were altered and the implementation delayed:
|
Message from Kathy Bergsma to CCC-L: The security checks for the wireless network will NOT be activated on Sunday as planned. The wireless network will work as it does today until further notice. We decided to allow extra time to register update servers that need access through the NAC for their managed laptops. If you manage a WSUS, SCCM, ePO or other patch management system that you want to have access through the NAC, please let me know by next Thursday, May 5. We prefer to keep the list small, so please consider alternatives that will deliver updates to your users over the wire. We also encountered a problem certifying users that pass the security checks for 7 days as promised. This feature of the product does not appear to work as promised. If the vendor is not able to resolve the problem, we will deploy the security checks without certification. This means that users will have to pass the security checks every time they connect, adding 10-30 seconds to the access time. We have not set a new date for activation of the security checks, but I hope to be able to provide more information by the end of next week. |
Dennis Brown mentioned having noticed via the Net-Managers list that the "session timeout on the Wireless authentication NAC system will be increased from 10 minutes to 1 hour." He was pleased as he expects this to make smartphone WiFi access less of a pain as users would not have to enter credentials so frequently.
UF Exchange Project updates (previous discussion)
Exchange 2010 migration status
Andrew said that they have been having conversations about moving IFAS to Exchange 2010. Earlier this week they were provided access to the Exchange 2010 Management Tools, which is a good first step. The next step will involve converting our distribution groups from Global to Universal as this is a requirement of Exchange Server 2010 SP1 [see "Caution" statement early-on in that page]. Andrew has a PS script to perform that conversion but wants to be cautious and needs to find the time to proceed on that.
The Exchange team will be at TechEd in Atlanta next week and Andrew has told them he will try to get that conversion done while they are gone.
Proofpoint configuration options changed
Dan Cromer had related via the ICC-L that the "high spam protection policy" has been added as an option to the ProofPoint anti-spam application:
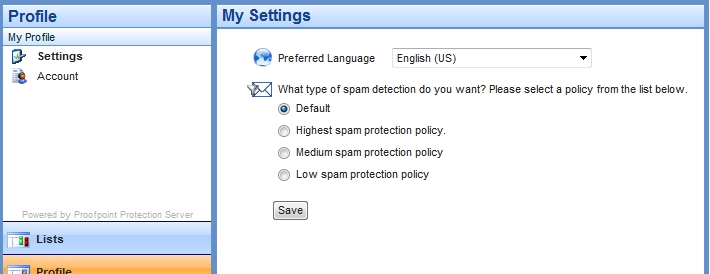
With this setting, messages scored 80-100 are deleted while those scoring 50-79 go into quarantine. These changes have been documented (sans a new screenshot of the settings page as shown above) at http://www.mail.ufl.edu/proofpointsettings.shtml.
Centralized FAX service via Exchange (previous discussion)
Updates not available...
Sakai e-Learning System now in production (previous discussion)
Updates not available...
IT survey is coming (previous discussion)
We will keep this topic on our agendas until some resolution occurs.
Alternate IFAS domains in e-mail
Updates not available...
Electronic Copy - Print Output Cost Reduction program (previous discussion)
Updates not available...
myuf Market (previous discussion)
Steve wants to keep this on our agendas in case discussion seems warranted.
Split DNS solution for UFAD problems
Steve wants to keep this on the agenda for future reference.
Wayne Hyde mentioned that one hold up for Santos relates to getting enough virtual infrastructure space to support his project. Once we get the new virtual infrastructure in and running, then Santos will be able to go ahead with his stuff.
Mike Ryabin asked Andrew about when he might expect the new MPS to be implemented on the virtual server machine at Ft. Lauderdale. Andrew responded that the schedule was "fluid" at the moment. He is still trying to tackle those sites which are experiencing hardware failure of the older machines or are strapped for storage space. Andrew's best guess that this was still several months away for Ft. Lauderdale, however.
Mike related his main concern was that their phone system utilizes that DHCP server and he wants a smooth transition. Andrew assured him that the transition, when it comes, would be smooth.
Andrew said that as they began deploying the new MPS configurations to some of the bigger RECs, they realized that more space was required. A number of locations have one or more out-of-date servers which have been serving as supplemental file servers and it was decided that now was a good time to consolidate those into a more robust and centrally-managed solution. The beauty of the virtual architecture being used for MPS deployment now is that transitioning to a new hardware platform is much simpler.
These expanded MPS servers are being instituted at IRREC in Ft. Pierce, MREC in Apopka, NFREC in Quincy, TREC in Homestead, and GCREC in Balm/Wimauma. These larger MPS machines will range from 5.5TB to 7TB in storage using RAID 6 with 2TB drives. They were able to provide a bit more space with these because a back-up drive was not included; these sites have good connectivity and are being backed-up to Gainesville via DPM. Andrew noted that there are about seventeen MPS servers yet to be deployed overall and the current newly deployed MPS at these larger sites can be redeployed elsewhere once they are upgraded.
Wayne Hyde said that Matt Wilson has moved all the "easy" database over to the new cluster. They are still waiting on SharePoint to get off the old virtual SQLserver.
New virtual infrastructure being planned and spec'ed out
ITSA had submitted the quotes/lease proposal for approval for the new SAN and virtual infrastructure--including a 10 Gb network. The SAN portion is now being renegotiated, however. It was originally going to be Dell/Equallogic, but then EMC offered better price on the new VNX platform that is arguably better technology. The VNX platform supports SSDs which will allow us to utilize those in the SAN to support virtual desktop replicas. Wayne also intends to utilize SSDs for cache. These moves should greatly enhance performance. Our current SAN is the CLARiiON CX3 which was replaced by the CX4 and now the VNX; thus we will see a two generation jump ahead with this upgrade. There will be considerably more storage space for our file services so we will be able to consolidate those to a great extent.
The bottom line is that the new SAN will have more space and more speed for less money than originally planned with the Equallogic proposal. This means we can spend that savings on the virtual infrastructure itself. Consequently, there will be ten R710 servers with 192GB RAM each -- five for VDI, five for servers. That VDI expansion should allow opening VDI up to all of IFAS for certain purposes.
There will be two Juniper 48-port 10Gb switches. Wayne has 100 VMWare View licenses for our VDI which allows 100 concurrent users. Wayne wants to try to open up some pools to all ifas faculty/staff and is trying to get a list of software that is needed. Right now, for all VMs it will have as a base: acrobat reader, flash player, java, silverlight, microsoft office and stuff that is essentially free, including ArcGIS, R and JMP.
The new equipment will allow consolidation of most everything into three-four racks and should provide considerable savings on power and cooling.
Wayne reiterated that this new infrastructure will be quite capable of support any unit-server needs and there should be no reason for any unit to have to purchase their own servers as such things can be more cheaply and efficiently be supplied centrally.
There continues to be no progress on the documentation which was to happen prior to announcement. Since this has never been formally announced, the matter remains on the agenda as a standing item.
Windows 7 Deployment via the WAIK, MS Deployment Toolkit 2010, USMT 4.0, WDS, and SCCM
Updates as available...
UF SCCM Support Group
Updates not available...
Exit processes, NMB and permission removal (prior discussion)
Updates not available...
Re-enabling the Windows firewall (prior discussion)
Updates not available...
Services Documentation: Is a Wiki the way? (prior discussion)
Updates not available...
Recording lectures for Distance Education (previous discussion)
Protected access for captured lectures
Steve would like to address this issue once Santos is available for discussion.
New DHCP reservation site created (previous discussion)
You are reminded that Santos Soler has created a new DHCP reservation site which you may use to request reservations. Dennis Brown mentioned having used the site successfully and Steve added that he had utilized it just yesterday. Santos prefers that we use this rather than e-mail him separately.
Restoration of back-ups on the file server
Wayne Hyde intends to document and announce proper usage as time permits.
Membership of ". IFAS-ICC" e-mail distribution group to be narrowed to ICC members only (previous discussion)
Steve will keep this as a standing item on our agendas for now as a reminder. The ICC distribution list is more targeted and restricted to IFAS IT support folks only.
IFAS efforts toward Green IT (previous discussion)
Updates not available...
Creating guest GatorLink accounts: singly or in bulk (prior discussion)
Steve had left this on the agenda in case further discussion was deemed warranted.
Can IFAS support DirectAccess in the future? (prior discussion)
Steve wants to keep this topic on our radar.
Moving away from the IFAS VPN service (previous discussion)
Dan Cromer would like to “greatly” reduce the number of IFAS users who use the IFAS service by shifting them to the CISCO Client or native L2TP connection hosted at CNS.
Dan noted that we get UFIRT security reports up to several times a day from people using the IFAS VPN with compromised/unpatched/vulnerable machines. Dan's main concern is the burden on Wayne as ISM. We also get a report from UF Security Team about the number of incidents that we have, which goes to Dr. Joyce, and Dan would like to cut down on the number of incidents.
Dan added that our incident response time and control of number of compromises is very high compared to others at UF, so kudos to Wayne and many in ICC for that.
Dan wants to set a date by which we are going to allow access to the IFAS VPN only via special justification. Access is currently allowed to "_ifas-users_autoGS" and we have ". ifas-vpn external users" and ". ifas-vpn blocked users" groups to handle exceptions. This would change to a " ifas-vpn allowed users" when more tightly controlled access was implemented.
Dan mentioned that he prefers the L2TP solution (as do most others) because nothing need be installed (configuration only) and he has found it works better for some things.
Steve wondered about IFAS starting to use CNS's departmental VPN tunnels where our users were provided a given range of VPN addresses. He asked if that would send these incidents right back into our lap. Wayne responded that CNS would kick people off the VPN service and not leave that up to Wayne to track them down.
Dennis pointed out that he still wants to know if his users are causing UFIRT notifications and Wayne suggested these would likely continue based on the username of whoever was connecting.
Dennis noted that CNS seems to prefer the Cisco client and asked if they intended to remove support for L2TP. Dan Cromer responded that CNS has nixed that idea since there is no Cisco client for quite a number of smartphones.
Steve also wanted to point out that the documentation on the Net Services web site covers XP and Vista but not Windows 7. The items that need setting have moved enough that new documentation is needed. Steve has asked Dan Miller who to contact about updating that. Steve's own re-write of those instructions follows:
Dan noted that this change to the IFAS VPN service will require proper notification and should likely go through ITPAC for approval. Based on our discussion, the ICC approves of this change provided sufficient notification is made prior.
VDI desktops as admin workstations (previous discussion)
Updates not available...
Wayne's Power Tools (prior discussion)
Updates not available...
Computer compliance tool in production (previous discussion)
Updates not available...
Folder permissioning on the IFAS file server
You are reminded to please take the time to read and implement the new standards. If you have any questions get with Wayne or Steve.
Disabling/deleting computer accounts based on computer password age
This is yet another matter for which finding time for implementation is proving difficult. Steve wants folks to remember that Andrew Carey has a good plan for dealing with this which he simply has had no time to address. In the meantime, it would be very good of each OU Admin to consider mimicking the proposed plan manually by keeping their own records and deleting any computer object which have been disabled for 90 or more days; Wayne's Power Tools can identify those. Steve has finally begun doing that for his own unit and it has made his view within ADUC much more agreeable.
Core Services status (previous discussion)
see the new virtual infrastructure section above...
Updates not available...
Status of SharePoint services (prior discussion)
IFAS migrating to centralized MOSS
Updates not available...
Public folder file deletion policies and procedures status
Nothing further was available on this topic at this time.
Microsoft
The May Microsoft patches included two bulletins (one "Critical" and one "Important") covering several vulnerabilities for Microsoft Windows and Office.
McAfee provides podcasts on the highlights of each month's offerings and another podcast summary of these patches is provided by "Security Bulletins for the regular IT guy".
Adobe
Adobe released yet another batch of out-of-band security patches for Adobe Reader and Acrobat. This was related to the Flash issue mentioned last month. Yes, Acrobat and Reader contain their very own copy of Flash. They might want to re-think things. Version 10 of Reader will be patched later because Adobe is assuming "Protected Mode", which most have to turn off to get things to work, will protect users.
...and just when one might think progress was occurring, yesterday they released ANOTHER security update for Flash Player. The activex version is now at 10.3.181.14. [See details of remote patching solution.]
Oracle
JRE 6 Update 25 was released during the middle of last week. This is a performance improvement, however, rather than a security update.
Wayne Hyde noted that IFAS has had quite a few Java vulnerability notices that are still not contained (10-15). Wayne urged OU Admins to follow-up on those notices and get the systems patched/rebuilt as necessary. Attending to those tickets on a timely basis will avoid Wayne having to set a DHCP restriction that would effectively disconnect those machines from the network.
MS Office News update
Steve had reported via the ICC distribution list back in mid-April concerning Print issues in Outlook 2007 after installing KB2509470. Microsoft has since released a hotfix.
Job Matrix Update status
This is here as a standing topic--no discussion this month.
Remedy system status (previous discussion)
Updates not available...
usage of the UF IT Alerts Dashboard page by IFAS
Updates not available...
RODC issues at remote sites (prior discussion)
Chris Leopold reported that UFAD has some sort of systemic issue that had actually been noticed by Mike Kanofsky about one year ago. A machine joined to UFAD should receive and apply its "IF-Co-Managed Computer" GPO from a local DC within its own site--depending on where it sits in the OU structure and that part seems to be working properly. On the user side, however, they are noticing that the "IF-CO-Managed User" GPOs often gets pulled from some other location. They believe this unexplained event explains why the User GPO application sometimes fails and drive mappings do not occur at times.
When drives fail to map on a machine, you can easily get diagnostic information. You just need to open a command prompt and type "gpresult /v > gpresults.txt". The resulting "gpresults.txt" file will contain a "Group Policy was applied from:" line telling you which DC was contacted for the user settings. When those are pulled from a remote DC, the "Login Scripts" policy is not applied for some reason.
The inconsistent nature of the problem has made it very difficult to track down the cause. Microsoft has been contacted about the issue by OSG and Chris has been accumulating data for them to examine. This has been happening both on- and off-campus apparently, but Chris believes this is the same problem that Kevin Hill began to notice with the deployment of the RODCs.
A current work-around is to run the login script manually from the netlogon share.
UAC settings egregious for users?
Updates not available...
PDF-Xchange (prior discussion)
Updates not available...
The meeting was adjourned early a little at about 11:30 AM.