

 |
 |
ICC Meeting: |
IFAS COMPUTER COORDINATORS
|
|
Message from Steve Lasley to security-l@lists.ufl.edu: Greetings, I've been trying to learn about using the recommended PGP WDE and have run into a number of questions/problems with implementation in our environment. Am I correct in assuming that this group is the appropriate one with whom to express these difficulties? If not, could you kindly direct me elsewhere? If so, are any instructions planned on how to implement this PGP WDE on a laptop with multiple users? I am puzzled how that is envisioned to work in our environment. Even access by administrative accounts (let alone by multiple end users) seems precluded under the simplistic instructions provided at https://infosec.ufl.edu/itworkers/pgp/pgpinstall.shtml or discussed in the October workshop. Assistance with that as well as detailed instructions for recovery procedures within our environment would seem very useful for all IT folks here. Thanks, |
Steve understands that such a request might easily slip through the cracks, but the end result was that Steve decided the transparency and ease of BitLocker encryption made it a superior choice. As a result, Steve by now has encrypted (nearly) all of his laptops with BitLocker; his concern there, however, is the reporting capability which is currently lacking.
PGP experience viewed as good from central perspective but still a mystery to most IFAS IT support folks
Dennis Brown asked what the overall experience has been with PGP and Avi responded that we currently have over 4000 laptops encrypted with the product. Avi was aware of very few problems. Upon hearing that we didn't feel enough training materials had been made available Avi asked what he might be able to do to improve that. Jimmy Anuszewski stated his feelings that as important as encryption is that he feels we should have annual workshops or at least something on-line that we can review as needed. Wendy Williams agreed that yearly encryption seminars would be good; they would serve as refreshers for non-security experts as well as for incoming IT support staff. Additionally, they would serve to keep us current with the constantly changing technologies and regulations.
Rob said that he would investigate offering a training session and recording that in a fashion modeled along the lines of the recent ITSM 101 session and providing three-pronged coverage of encryption via BitLocker, FileVault, and PGP WDE. Rob told Wendy that this would be a good topic to bring up at the next Campus IT Directors meeting and she promised to get that on the agenda.
Avi added that the Campus IT Directors had previously asked them for a single place to check for information on the subject of mobile security where they could share experiences and ask questions. They decided to host that on the UF IT Wiki. Avi said that there is not too much available there yet but that they would be a good place to collaborate on potential solutions.
Getting access to devices can itself be problematic
Winnie Lante said that while she plans to encrypt all new laptops as they come in, it is very difficult for her to get faculty to let go of current laptops long enough for her to get that done on all.
A plea to hold off a bit until tools are in place
Kevin Hill said that he supported the goals of the Policy and Standard but hoped that compliance could be considered a "best effort" basis until IFAS had the tools in place to implement this in a wholesale manner. Rob responded that "the policy is what it is." This has gone through the process and the dates are what they are; you are either in compliance or you are not in compliance. Rob said that they have tried their best not to mandate a particular technology and yet provide a solution so that this wouldn't be a completely unfunded mandate. Obtaining a PGP WDE license for the entire university and providing a server and Help Desk support for the product was the result of that. Elias can't and won't, however, fund everyone running around and installing this on everyone's laptop.
Help on the way for those using native BitLocker and FileVault encryption
Rob said that PGP has plans, currently in beta, to support reporting of native encryption status. The release date is not firm and has been moving around as these things often do, but the hope is that sometime in the Fall we will have an agent that can report on BitLocker and FileVault 2 native encryption, thus potentially allowing those methods to be policy compliant. It was less clear, however, if that agent would provide FileVault key management.
Steve asked the very practical question of whether instead of switching all his encrypted laptops from BitLocker to PGP WDE that it would be reasonable to keep them on BitLocker until this new PGP agent was available. In response, Avi explained that Rob has been working with General Counsel to put together some documentation requirements for those using native encryption that doesn't meet all current Policy dictates and that would hopefully protect UF should something happen. Rob said that there currently is no case law for a Safe Harbor provision on anything that is not like the PGP solution, but Rob said that he understands our issue and realizes that we are all doing our best to protect the university's data and systems. He asked Counsel how he can tell someone who has taken the effort to encrypt a device that it's not good enough. The result was the development of a documentation exercise that we need to go through in order to use products such as FileVault and BitLocker that will put UF, according to the Counsel's Office, in the best defensible position. This will be announced soon.
At this point with the native encryption documentation details soon to be released, along with the fact that a PGP management agent is supposedly soon to be coming, Rob felt that it was better to go ahead with in-progress native encryption then to change horses in mid-stream. Rob personally prefers a native encryption solution and understands why we might have gravitated in that direction.
Other potential mitigations to help in the interim with native encryption compliance
Steve mentioned that IFAS utilizes a Policy Compliance Checker tool that runs at logon and checks various things. It might be fairly simple to add-in an encryption status check. Although that would only work at logon it might help assist with compliance in the meantime. If UF had DirectAccess implemented [hint, hint] this could even provide a solution for laptops outside our network. Avi added that something that ran as a system task could serve such a function as well; Ira Harkness had worked out some methods of doing that which Avi said he could share with us should we be interested.
[Note: Wayne told Steve via chat after the meeting that an upcoming version of Lansweeper (not yet available) will include reporting on TPM and BitLocker.]
Ongoing PGP support
Winnie Lante mentioned that she has some laptops lacking a Trusted Platform Module (TPM) for which she will still need to use PGP. Avi noted that a PGP Install Guide is available on-line. He suggested contacting them via security@ufl.edu prior, however, because there is a little bit of setup that they need to do in order to make things go smoothly for us. That involves setting up policy group on the PGP server for each unit that provides administrative access for the local IT support person. This will allow one to define certain settings that will apply to all the laptops setup under that policy area; it will also supply the support person a backdoor account so they can access the laptop themselves.
[Note: Steve thinks it would be a good idea to add mention of this special "setup" either on the PGP Install Guide or elsewhere. He would also appreciate documentation on the best way to handle multiple users as well as some recommendations on how to handle non-domain-joined vs. domain-joined computers.]
Avi said that the actual install of PGP is quite simple and trouble-free. Avi also wanted people to note that Customer Technology Services (CTS) is taking over PGP support because the Security Office is not really into these kinds of operational things. That is still in the transitional stages but eventually that support will lie fully with a group that is better organized to provide such support. In the meantime, if you send the security team an e-mail they will help redirect your query.
Details on the PGP user experience
Dennis Brown asked about the transparency of PGP to the user. Avi responded that the only thing they will see is a PGP screen for entering their PGP passphrase. The standard install will sync this with their Windows password. Consequently, they will type in their Windows password and PGP will log them through the Windows GINA without having to enter them twice. At password change time, however, the user will have to enter the old credentials at the PGP screen and then the new ones at the standard Windows logon. This is because UF accounts/passwords originate within GatorLink outside UFAD; were that not the case then this aspect would also be transparent.
Kevin Hill asked about how multiple users are handled. Avi responded that one can define multiple users within PGP but it requires set up for each ahead of time, however, in order to define a PGP passphrase. [Note: This is the aspect of PGP in our environment that bothered Steve the most when he was investigating that solution back in 2011.]
Details relating to mobile devices
Whole device encryption is the name of the game with smartphones
Whole device encryption with a passcode is required on all mobile devices. The ability to wipe the device remotely is an additional requirement as well. Again, a particular solution was not mandated; however, most are using Exchange ActiveSync (EAS) which works well for this.
The challenges of mobile device encryption
With smartphones the key component for encryption lies with the device itself; the manufacturer must supply that. This was not built into the earlier versions of the Android operating system. Prior to that it was up to the actual manufacturers to provide that; some didn't and others did with varying degrees of success. Fortunately, with Android version 4.x that is now supported natively. Apple iOS has been pretty good since the introduction of the 3GS and iOS5. Windows Phone used to have encryption but they took it out. With Windows Phone 8 they put it back in but it can only be enabled by EAS policy. Unfortunately, they have discovered that turning on that EAS policy for everybody will break a number Android phones. Since there are a whole lot more Android phones than Windows Phones out there, they are in a quandary with regards to Windows Phones. Blackberry phones have always had great security support; the problem is that nobody likes them anymore.
End-user documentation for personal device encryption
Kevin Hill mentioned the need to have a location where smartphone users could be referred for information on what devices were and were not compliant. Avi responded that this was the intention behind the creation of the Mobile Device Compliance web page. This is meant to help end users take care of things for which they have personal responsibility should they be used for university business. Originally there were instructions here for FileVault and BitLocker, but those were removed because those methods do not meet the Policy requirements. Now that new documentation requirements are soon to be published, they should be able to restore those instructions to that site. The instructions for various platforms are available via buttons across the top or links within the "How" section.
Francis Ferguson said that he has a personal iPhone and an iPad for which the only possible restricted data they might contain would be in e-mail; other than that he does no UF business using the device. Francis asked if encryption was necessary in that case. Avi and Rob responded that yes it was but that this happens automatically when the device is configured to use UF Exchange via ActiveSync. If you do not configure UF Exchange the phone can still be easily encrypted via the setting of a passcode.
Help needed in keeping up with issues
Avi used to try to maintain a device compliance table but with the large number and frequent turnover of devices this proved impossible to keep up-to-date. The good news is that with Android version 4.x things have settled down to a fairly consistent state. Current versions of iOS are good. Current versions of Windows Phone are problematic. Avi stressed that should we notice anything that might be missing here (or on any of their sites) we should please let them know so it can be updated. If we have any questions about any of this please let him know and he will do his best to answer your questions first of all and then improve the documentation so everyone can see it.
Some data on our smartphone users is available
Avi mentioned that they had CNS pull data from ActiveSync showing users and what devices they are syncing. If we are interested in that data, please let them know. Steve pointed out that the https://helpdesk.ad.ufl.edu/ tool now provides that information on a per user basis as well (enter a username and see at page bottom).
[Note: As Wayne pointed out via a chat with Steve after the meeting, more detail may also be found within ADUC by enabling the "Users, Contacts, Groups, and Computers as containers" feature and drilling down into the UF > People branch to your OU, to a particular individual. Those who have enabled EAS on a device will have an "ExchangeActiveSyncDevices" folder with one or more entries for devices which they have connected. By right-clicking a device entry, choosing "Properties", and looking at the "Attribute Editor" tab, one may view numerous details of the device including model and OS version.]
Mobile Encryption Policy FAQ available
Avi pointed out that there is a Mobile Encryption Policy FAQ available to answer many of the common questions which arise as well.
Enforcement technology not yet mature
Dennis Brown asked about enforcement. Rob responded that they had really wanted to turn some technology on effective August 17th but the risk of doing so was too great. At the end of the day people need to get their work done and crippling the university was simply not an option. Unfortunately the technology, especially for smartphones, is currently insufficient. Rob personally likes the technology that sort-of split-brains the device into personal and work areas so that UF could remotely wipe the business-side without eliminating personal data that we all keep on such devices. These technologies have been slow to evolve, however. This is one of the areas that is being investigated by an Endpoint Protection Platform working group that has been working for quite some time under the lead of Geof Gowan of PHHP IT.
Details relating to mobile storage devices
This is the section of the policy that is perhaps most problematic
The Policy also requires full device encryption of mobile storage devices; this includes USB drives, external drives, and such. Rob asked if anyone had taken advantage of the USB trade-ins that have been offered. Francis Ferguson responded that this was a bit difficult to manage for those of us out around the state. Dennis Brown added that we generally have larger drives than those currently being traded. Avi pointed out that the reason behind the trade-in program was not to provide everyone with encrypted drives but rather to increase overall awareness. Dennis asked about remote wipe of those and Avi responded that such devices do not provide for any management.
Wendy Williams mentioned just learning that one of her users had purchased an external HDD; she wanted confirmation that this device must be encrypted if it is to be plugged into a UF computer. Avi responded that the answer was yes according to the Standard, but that this was a case where the technical solutions are somewhat lacking. Wendy asked if the Mobile Device Compliance web site had information on how to handle such devices and Avi responded that this web site was meant more for end users. Wendy said that this is where she has been sending people, but it is also where she has gone to get information. Wendy went on to say that this was one of the reasons she had wanted Avi and Rob to come talk with us today; we are all overworked anyway and we need help with learning new security techniques.
A revision of our procurement procedures is being investigated
Wendy asked about the issue that users can purchase and use devices without letting IT support know. Rob said that they are aware of this problem and that Elias has approached the CFO about possible solutions. Jimmy Anuszewski mentioned that he sends out regular reminders to his department that if they have purchased anything related to computers to please let him know because there are policies that apply to such devices. Jimmy said the reaction to that has been mostly positive. Rob said that if and until this can be resolved at a higher level that Jimmy's solution (along with documentation) is likely the best one currently.
Policy enforcement vs. personal responsibility
Kevin Hill pointed out that if IMAP (which can be utilized to avoid EAS) wasn't removed on August 17th that we have no way of ensuring that a smartphone doesn't contain restricted data. Avi responded that most of these policies do not have technical enforcement; this is still Policy and everyone is expected to comply. Rob added that there is personal responsibility: the University IT Regulations state that "Failure to follow University’s IT and Information Security Policies may result in penalties and disciplinary action, including but not limited to termination of employment or student expulsion, revocation of user access or other legal sanctions."
Documentation is our friend
Wendy asked if she was responsible if a faculty member refused, for example, to let her encrypt an external hard drive. Rob responded that she would not be responsible; rather that individual would be responsible. Avi and Rob said that the proper course to take in such circumstances would be to document the situation. You would send the individual an e-mail saying that you understand they have this device and you need to encrypt it for them. If the faculty refuses or doesn't respond then you follow up with a message informing them that they are violating the policy; Rob suggesting siting the regulation as well as that is where the "teeth" lay.
Third-party software patching
IFAS has failed to develop centralized third-party application patching procedures despite options being available
Wendy Williams raised the issue of her struggles with the SafeConnect posture assessment. We are asked not to make users local administrators on their machines but the posture assessment on wireless for laptops is now making it abundantly clear that our patching procedures are not yet mature enough to truly support doing that. While IFAS does use WSUS for Windows updates, individual IFAS units currently have little to no automated tools available to assist with third-party application updates. The Secunia software which UF purchased to provide the means for this is not made available to unit staff individually; with SWFREC as the single exception, all of IFAS utilizes a single WSUS server but doesn't have the centralized staffing available to manage third-party patching for all via Secunia. The plan has been to eventually utilize SCCM for that, but such efforts continue to be delayed by the slow progress of UF's centralized SCCM project. As a result, the majority of our unit IT support staff are either leaving third-party patching up to the end users or spending a great deal of time installing updates by hand themselves. The former doesn't get the job done and the latter takes time away from the support staff for addressing other important duties.
Edge Protection Project may provide eventual third-party patching solution
Avi pointed out that the EPP Project may solve our third-party patching issues eventually. The idea behind that was that we currently have all sorts of different agents working on various aspects of management; wouldn't it be great if we could find a single "one agent to rule them all" solution that could address all of those needs. This workgroup has been setting up proof of concept trials this summer with various vendors.
Wireless posture assessment issues
Regarding the wireless posture assessment, Steve told Avi of an experience he had that he shared with the ICC last month. Basically, it appears that the remediation procedures could really use some additional work. Steve also wished that the wider expertise of the UF Computing Help Desk on resolving wireless connection issues could be distributed out to unit support staff in some better fashion than is done currently. The way it is now, numerous folks are busily solving problems that are likely already well known by others. Avi suggested contacting Ayola about that to see if their Wiki might be better utilized to provide an answer to that problem. Avi also mentioned that everyone needing to "reinvent the wheel" is something that UFIT is definitely trying to solve, but again it is sometimes difficult for them to know what sort of problems we are running into. Avi's suggestion was to please make noise; that really helps them a lot. Avi spends a lot of time wondering what is it that he knows that others need to know as well, but it is difficult to evaluate the answer to that when viewing things only from his own perspective.
An invitation to visit a CEO
Francis Ferguson suggested that Avi might enjoy visiting a County Extension Office with him sometime just to see how different that environment can be. Avi said that as a student he actually worked in the CALS Dean's office and after that for the Department of Citrus traveling back and forth to Lakeland. He is aware that things have changed greatly since the early 90s but he is at least a little bit familiar with our scope of things.
Up until a few years ago Avi was with the Health Science Center and had started the security program there. That was a case where they had a federal law that was a very big driver and yet it was still a multi-year process. These things take time because we are changing the culture and the way people think about their computers and their access. Now we are trying to go through that process again with an even wider audience and with people that don't have that direct threat of jail time. The best thing we can do is keep up the channels of communication and remind people that these resources belong to the university and there are things that must be managed accordingly.
Avi sometimes sees his job as being akin to a marriage counselor. He has been dragged into many situations where there is a difficult faculty member and an exasperated IT Director and the IT Directors want Avi to just "make them do it." Avi can't make them but he will sit down and try every way they can to convince the person to do what they need to do.
Engaging our student population
Dennis Brown suggested that we need to find a way to engage our student population. Rob agreed that this would certain be an issue with our medical students and student workers; they will definitely be required to follow this policy. For the rest of our student population, however, Rob believes we need to update the Policy and this is on Avi's "todo" list.
Closing remarks
Avi asked that we please contact the Security group if they can be of assistance in any way. Rob and Avi both said that they would be happy to come back at the next meeting to continue this conversation if that would be useful. Avi even mentioned his willingness to return on a regular basis every few months just to keep us up-to-date on what is going on and provide us the opportunity for feedback. Wendy Williams and others all agreed that this would be wonderful. The ICC would like to thank both Rob and Avi for the time they spent with us this day.
[In order to make meeting participation more efficient for Patrick Pettus and James Moore, these two topics have been moved to reside at the top of our agendas.]
Videoconferencing topics (previous discussion)
Endpoint security concerns
Updates not available...
Replacing Polycom endpoints with some Lync-based solution (previous discussion)
Updates not available...
Possible end-point refresh in the works (previous discussion)
Updates not available...
Movi/Jabber Updates (previous discussion)
Updates not available...
Other standing VC topics
End-user Scheduling (previous discussion)
You may have noticed that the VCS web site was revamped on July 1st. Part of this change includes access to a new "Smart Scheduler web application that provides a simple front-end to TMS. This application allows selected individuals the ability to create VC events and tutorial videos have been generated to assist first-time users.
Correction as of 7/22/13: Steve later found out that permissions to use the Smart Scheduler are not tied to the email-enabled security groups currently as he had previously thought; rather, the Smart Scheduler is open to all "authenticated users".
The "Smart Scheduler" has a number of limitations:
These and other issues may be overcome either by requesting an event similarly to how it has been done in the past, or by going directly to the TMS console.
Correction as of 7/22/13: Steve later found out that Patrick does not intend to permit direct editing/monitoring via TMS at least initially; that may be opened up somewhat later but he wants training to proceed that. As a consequence, the details of direct TMS editing/monitoring below will not be available for the time being.
[Note: the main VCS will redirect http://video.ufl.edu to https://video.ufl.edu. This is not the case with the TMS console, so you will will want to be careful to utilize the https protocol on the latter.]
There are a number of "tricks" that one will need to learn when using the TMS console, including how to add incoming and outgoing video calls via IP# or URI. Being able to manage the buffers, etc. makes this well worth the effort in Steve's opinion. Furthermore, the direct TMS editing, monitoring, and control capabilities (which require JRE *boo*hiss*) are a huge bonus as well:
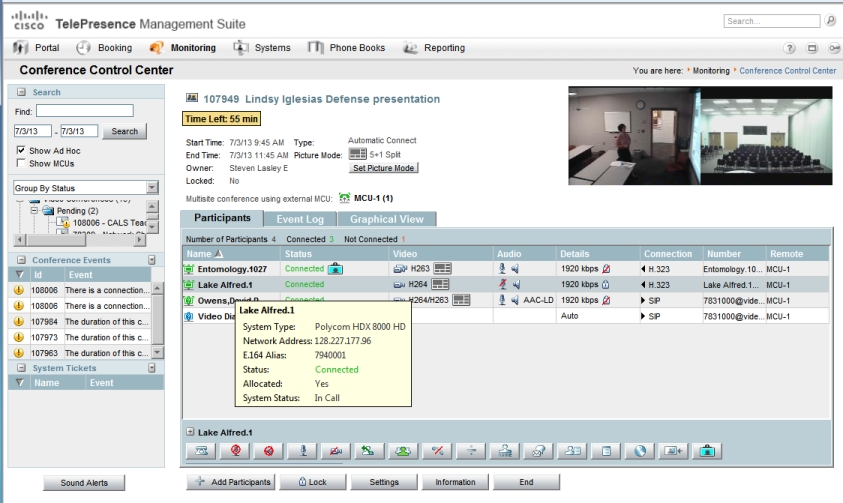
Here you can view the event log for the VC, control audio and video muting of each site, add/remove participants, control layout, and extend the length of an ongoing VC among other things. Very cool. It can turn you into a mini-Dean Delker. :-)
Steve would like to remind folks about the VC email notification groups that were discussed at our last meeting. It is time for OU Admins to begin populating those groups with the accounts of the appropriate personnel in each of our units with videoconferencing endpoint.
Lync updates (previous discussion)
Updates not available...
SIP may replace H.323 as preferred protocol for endpoints (previous discussion)
Updates not available...
WAN (previous discussion)
Updates from James Moore
Updates not available...
Wireless printers
We hope to have James Moore and perhaps Nancy Watson and Matt Grover join us at an upcoming meeting to provide some updates on Flex Connect and local wireless authentication. In the meantime, James shared via em-mail that Nancy is about finished with Flex Connect and would like to deploy additional APs to Immokalee, which James Moore will fund. They feel that Immokalee is a good choice and Kevin Hill is a good candidate for helping them test the Nancy's design. Also, Matt is looking at creating a private WLAN for wireless printers to live. He is working on designing this type of access for campus & DE sites now and he will update the ICC very soon.
Also, Wendy Williams is excited about her recent investigation of a Pcounter replacement; this is the print metering/management software which they use in their student computer lab. The product being investigated is called Papercut and that works with another product called Presto from Collobos software. This software supports printing from mobile devices (Android, iPad, or iPhone) based on Active Directory accounts and permissions. Since Presto is licensed per-server, Wendy is hopeful that she may be able to buy one license for the IFAS print server that can support all of IFAS.
VoIP at RECs
Updates not available...
Phone bills to be paid for centrally? (previous discussion)
Updates not available...
Notes from June SIAC meeting
The notes from the June SIAC meeting is now available.
June's IT Directors Meeting Notes
The notes from the June Campus IT Directors meeting are now available.
UF Authentication Management Policy and Standard and Password Complexity Standard (previous discussion)
Rob Adams had sent out the following announcement on June 29th:
|
UF's Information Technology Governance has recommended a new UF Authentication Management Policy and Standard and a Password Complexity Standard, which have been approved by the VP and CIO. An Administrative Memo announcing the new policy will be issued the week of July 15, 2013. Highlights of the new policy and standards are:
UFIT will enable the technical changes required to implement this standard on UFIT provided services on July 14, 2013. After that point, users will be able to create passwords containing up to 48 characters, which may lead to authentication problems if systems cannot handle long passwords. The Campus IT Directors have been involved with the vetting of the policy and standards and have been asked to vet them with their constituencies. We have stressed the importance of testing college and department systems to verify compatibility with long passwords so as not to cause service disruptions for users that choose to use them. If you have information systems that do not use Shibboleth or native Active Directory authentication and have not yet tested long passwords, I urge you to do so immediately. If you have any questions about these changes and/or require assistance, please contact Avi Baumstein (avi@ufl.edu). |
PrintSmart initiative (previous discussion)
Santos Soler made the following announcement as a means for being proactive about the new UF PrintSmart initiative:
|
We have received a couple of the new Xerox MFP’s and they are working fine. In order for the setup to be completed in a timely manner we need you to be prepared with the following information. I will need:
You will need:
If this is done prior to the arrival of the machine it is mostly a plug and play setup and just configuration. Make sure when the device is setup that YOU test all the enabled features before the tech leaves. |
New IT Service Management Initiative
There was a "ITSM 101: What Every IT Professional Should Know" presentation on July 9th; the recording and PowerPoints are available here.
Implementing the Mobile Computing Security policy (previous discussion)
Updates not available...
Content Management System (CMS) for UF: Entering purchasing phase
Recorded sessions from demos by the three potential vendors for UF's new Web Content Management System (WCMS) are now available. Jimmy noted that the sandbox committee voted for TerminalFour with Adobe running an extremely close second. Oracle apparently drew some vigorous criticism.
Authentication Management policy draft (previous discussion)
Updates not available...
New 'Trouble-Ticket' Entry Page for CNS (previous discussion)
Updates not available...
KACE (previous discussion)
Updates not available...
CNS working to implement NAC for UF wireless (previous discussion)
Updates not available...
UF Exchange updates (previous discussion)
Outsourcing of student e-mail?
Updates not available...
Outlook asking for re-authentication
Updates not available...
Sakai e-Learning System now in production (previous discussion)
Updates not available...
Alternate IFAS domains in e-mail (previous discussion)
Updates not available...
Split DNS solution for UFAD problems (previous discussion)
Updates not available...
New web cluster (previous discussion)
Updates not available...
Windows 8 Deployment? (previous discussion)
Updates not available...
SCCM for IFAS
Work continues on the central SCCM plans.
Updates not available...
Exit processes, NMB and permission removal (previous discussion)
Updates not available...
Services Documentation: Is a Wiki the way? (previous discussion)
Updates not available...
Moving from McAfee VirusScan to Microsoft Forefront Endpoint Protection?
Updates not available...
Print server (previous discussion)
Updates not available...
Recording lectures for Distance Education (previous discussion)
Updates not available...
New DHCP reservation site created (previous discussion)
You are reminded that Santos Soler has created a new DHCP reservation site which you may use to request reservations.
Restoration of back-ups on the file server
Wayne Hyde intends to document and announce proper usage as time permits.
Membership of ". IFAS-ICC" e-mail distribution group to be narrowed to ICC members only (previous discussion)
Steve will keep this as a standing item on our agendas for now as a reminder. The ICC distribution list is more targeted and restricted to IFAS IT support folks only.
IFAS efforts toward Green IT (previous discussion)
Updates not available...
Creating guest GatorLink accounts: singly or in bulk (previous discussion)
Steve had left this on the agenda in case further discussion was deemed warranted.
DirectAccess pilot (previous discussion)
Updates not available...
VDI desktops as admin workstations (previous discussion)
Updates not available...
Wayne's Power Tools (previous discussion)
Updates not available...
Computer compliance tool update (previous discussion)
Chris Leopold rolled out version 2.1 of the IFAS Policy Compliance Checker on June 18th. This software now provides checks for:
Chris is expecting to update the documentation shortly.
Folder permissioning on the IFAS file server (previous discussion)
You are reminded to please take the time to read and implement the new standards. If you have any questions get with Wayne or Steve.
Disabling/deleting computer accounts based on computer password age (previous discussion)
This is yet another matter for which finding time for implementation is proving difficult. Steve wants folks to remember that Andrew Carey had a good plan for dealing with this which perhaps Alex York's replacement can find the time to address eventually. In the meantime, it would be very good of each OU Admin to consider mimicking the proposed plan manually by keeping their own records and deleting any computer object which have been disabled for 90 or more days; Wayne's Power Tools can identify those. Steve has finally begun doing that for his own unit and it has made his view within ADUC much more agreeable.
Since BitLocker stores its keys within the computer object in UFAD, Chris Leopold was considering scavenging those keys for secure storage elsewhere. That would provide a fallback for decrypting a drive should the associated computer object be deleted.
Core Services status (previous discussion)
Updates not available...
ePO updates (previous discussion)
Updates not available...
Status of SharePoint services (previous discussion)
IFAS migrating to centralized MOSS
Updates not available...
Public folder file deletion policies and procedures status (previous discussion)
Updates not available...
Patching updates... (previous discussion)
Microsoft
The July Microsoft patches included 7 bulletins (6 "Critical", and 1 "Important") covering 34 CVEs in the usual suspects. A risk assessment is available here.
McAfee generally provides podcasts on the highlights of each month's offerings.
The Enhanced Mitigation Experience Toolkit 4.0 is now available. IFAS may wish to consider deploying this via GPO as a means to mitigate vulnerability exploits.
Adobe
New security updates of Flash, Shockwave, and Cold Fusion were released on Tuesday.
Also, apparently Adobe Reader 11.0.03 installs multiple vulnerable components.
Java
Oracle has finally pulled the plug on JREv6 security updates with the release of JREv7u25 on June 18th. This latest release fixes over 34 vulnerabilities leaving only a billion more. ;-)
other news
Some of you may have interest in Google's latest Transparency Report which provides data about trends in unsafe websites and Google's efforts to making browsing safer.
MS Office News update (previous discussion)
Updates not available...
Job Matrix Update status (previous discussion)
Updates not available...
VP communication frustration
At the tail-end of the meeting Dan Cromer shared an email that our VP had just sent to the IFAS Chairs and Center Directors:
|
Message from Jack Payne to the Deans and Center Directors: Dear Chairs and Center Directors, Most of you have a list serve for which we can communicate with all the members of your Department/REC, which usually have the structure that begins as follows: . ifas hort faculty or . ifas crec, etc. However, a good number of you do not. It is very frustrating when I need to communicate a decision and/or information to a department or center faculty and cannot find a legitimate list serve. Most recently this morning I needed to communicate an interim chair decision to an IFAS department that had no list serve listed. I called the Department and asked AA, who was a substitute and didn’t know. I then asked the interim who gave me an address that didn’t work. The AA then gave me a list serve that wouldn’t work because it was restricted. I then wrote the outgoing chair, who replied that he would work on it right away – so you get the picture. I am asking that you all make sure that you have a list serve listed in the . ifas format that can easily be found by clicking on the “To” button in an email address. At least have one for all faculty, then one for staff and then one for all employees. I assume that you need to coordinate this with your IT person. Dan, please make sure that this happens. THANKS!!! |
Dan was apparently as surprised by this as we were. Later that day after some feedback via the ICC, he responded to Dr. Payne as follows:
|
Message from Dan Cromer to Jack Payne and the Administrative Council: Dear Dr. Payne, We have a large number of distribution lists, using several mechanisms, that have been developed over the years. Some lists are derived from membership in the IFAS Directory, others are manually maintained. Some have been maintained well, others not so well. You are the first senior administrator who has wanted to use the system as you do, so this hasn’t been a priority in the past. I understand that the priority has changed. Please be patient with me as we reorganize the system so that department membership will be derived from HR records, which will make sure that people in a department will be included without manual updates. I will work first with those departments whose administrators have already contacted my department for assistance. Dan |
Dan then wrote again to the ICC with his recommendation on how best to proceed:
|
Message from Dan Cromer to the ICC-L: Dennis and all, I’ll not make any decision on this until getting discussion on this list, and would certainly prefer consensus. There are several ways to go, but I don’t think we should consider any method that requires manual updates; one is using the People OU to define the list of addressees. On the other hand, the IFAS Directory offers many benefits, and is already used for many lists, some of them explicitly for departments. This makes one approach, then, to automate the update of the IFAS Directory core information, with Liaisons only responsible for the extra information. This latter approach would be my preference, as I have long wanted the Directory to be accurate, at least as far as names, emails, and departments are concerned. I have a love/hate relationship with Listserv. The biggest benefit is that it provides for easy configuration for archive, and anyone with an email can be on a list. This latter feature hasn’t been easily met otherwise. Winnie asked about the list names starting with “.” Remember that the Display Name is separate from the list name. I think we’re stuck with the naming convention of starting with “. IFAS” for the Display Name, with the true list name having no leading period, so all Display Names should follow that convention. Please respond with your thoughts. Dan |
The meeting was adjourned a bit late just after noon.