

 |
 |
ICC Meeting: |
IFAS COMPUTER COORDINATORS
|
|
Message to the IFAS-Announce-L from Mark Rieger: The Elluminate Live Manager (ELM) system will be phased out in favor of the Elluminate Session Administration System (SAS) as of May 10, 2010. If you are a current Elluminate user, we have already migrated your account from ELM into SAS. If you are not currently an Elluminate user but anticipate that you will be using it in the Summer or Fall, please contact Ron Thomas to receive an account at no cost to you. If you are a current Elluminate user under ELM and have made recordings that you want to continue to access after May 10, please contact Ron Thomas immediately. And finally, if you are a current Elluminate user, please use the SAS interface to schedule any new sessions (https://sas.elluminate.com/site/external/login/user). |
Dan Cromer had also forwarded a message from Scott Blades, UF College of Pharmacy, where Scott pointed to a video series he had created that covers a number of topics IT support and their users may find helpful. A SAS training session script was attached. Dan cautioned that Scott supports Pharmacy only, however, and any questions IFAS folks might have should go through Ron Thomas.
WAN transition to CNS (previous discussion)
Updates from James Moore
James asked that his report be delayed until later in the meeting, but the results of that will be reported here so as to not change the structure of the notes. James offered the following updates:
Alternate IFAS domains in e-mail
Steve wants to keep this on our agenda for future discussion. He believes there is no advantage to having multiple aliases and that we should move towards removing those if possible.
It was announced Tuesday that Elias Eldayrie has been selected.
Identity Management (IdM) Interface Training via Polycom, Wednesday, March 17th at 2:30-4:30 PM
Whether or not you missed this training session, the handout is now available. Other related policy, background and standards documents are likewise available.
Your Department Security Administrator can now request the role which will allow you to set NMB for your users. The role to request is "UF_PA_IDM_NETMGR". If you had been a Directory Coordinator prior and want to back off a bit there is also a "UF_PA_IDM_ID_VIEWER" role which will allow you to browse but not change things.
ITAC-NI still meeting (previous discussion)
The committee meeting this month was delayed a week, so we will be meeting next Thursday. The meeting will involve a demo of the Health Center's new Cisco videoconferencing system. A few day afterwards Steve intends to make the draft minutes available.
Course Management System Conversion to Sakai 3 (previous discussion)
Steve reminded folks of Doug Johnson's announcement of a CMS Transition web site. Doug had indicated that this site expands upon the official IT project site.
myuf Market (previous discussion)
Steve wants to keep this on our agendas in case discussion seems warranted.
UF Exchange Project updates (previous discussion)
Centralized FAX service via Exchange (previous discussion)
Steve wants to keep this potential service in everyone's minds as it seems a logical direction for all to take.
Office Communications Server (prior discussion)
In response to a query from Joel Parlin, Dan Cromer reported on the status of this via an e-mail earlier in the week:
|
Message to the ICC-L from Dan Cromer: All, E-CALS for all faculty and staff were purchased effective April 1. Thanks to quick work from Wayne to create the list, I have entered all IFAS accounts into the script to SIP-enable them for Microsoft Office Communicator, so OCS software should work for all. The major announcement and publicity about OCS availability is waiting on the production OCS server environment (two edge servers behind load-balancing Cisco, two main OCS servers), which is expected sometime in May, but the "pilot" environment, with single server, is still available. Software files, along with installation documentation, is [sic] at \\ad.ufl.edu\IFAS\Software\OCS. Dan |
Steve asked how that process (SIP enabling) would be handled for new accounts in the future. Dan responded that he didn't believe the details of that had been worked out but he intends for Scott Owens to handle that when new mailboxes are created. Dwight Jesseman responded that he is waiting for Mike Conlon to make the decision as to exactly who is to be SIP enabled. Dwight doesn't have a clear group in UFAD to choose from for that as there is no "employees" group available at this time.
Split DNS solution for UFAD problems
Steve wants to keep this on the agenda for future reference.
There continues to be no progress on the documentation which was to happen prior to announcement. Since this has never been formally announced, the matter remains on the agenda as a standing item.
Windows 7 Deployment via the WAIK, MS Deployment Toolkit 2010, USMT 4.0, WDS, and SCCM
login script changes to accommodate Windows 7
As far as Steve has heard, the changes have resolved earlier known issues.
Printer mapping issues
Steve believes that Andrew Cary feels this problem has been identified and resolved.
Issue with offline files and folder redirection
Steve mentioned having experienced logon delays for Windows 7 machines using folder redirection to put user documents on the file server. Andrew has been assisting in diagnosis. This problem is related to the use of offline files somehow and has been discussed in the Group Policies section of Mark Minasi's Reader Forum.
Windows 7 deployment
Daniel Solano resolved the PXE boot issues and Steve is now able to deploy images from the SCCM server. Steve presented a brief overview document that Daniel had done and wanted to discuss how that service might meet the needs of all. SCCM is very complex and obtaining training for Daniel would be a good investment should funds ever be available.
Exit processes, NMB and permission removal (prior discussion)
Nothing further was available on this topic at this time.
Re-enabling the Windows firewall
Wayne Hyde has this on his schedule for after the SAN upgrade (which begins next week) is completed.
Services Documentation: Is a Wiki the way? (prior discussion)
Steve skipped over this topic but will keep it on our agendas.
Enabling passthrough authentication for http://*ufl.edu and https://*ufl.edu via GPO
This topic was discussed last month under the heading "Avoiding the logon screen security message with the MyUFL splash screen". Kevin Hill's proposed GPO solution is not appropriate for most of us due to it interfering with GPP processes in the "IF-Co-Managed User" GPO. Using Kevin's solution would remove the "file://ad.ufl.edu" setting it supplies and those using Windows 7 will start getting prompted via dialog box (Open File - Security Warning) to run the various logon script files. Most annoying.
Steve has come up with the GPP equivalent (with a good deal of help from Andrew):
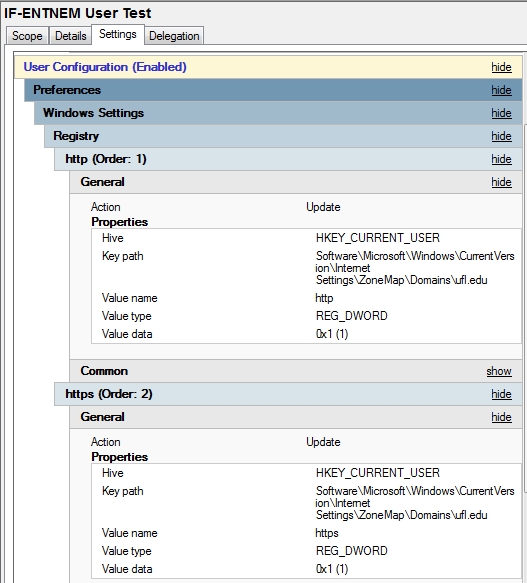
Solving the original issue which David Bauldree raised would also entail setting the following:
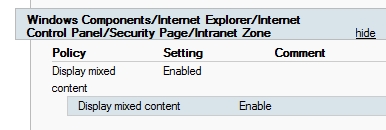
Steve has already implemented this latter portion for his own unit via a GPO Administrative Template. This overcomes mixed content prompts for poorly written sites within the Intranet Zone.
Adding the wildcard entries to the zone list would remove all sorts of annoying prompts when accessing protected websites and would no-doubt be appreciated by our users if the security risk was not deemed too great.
Should this be done for our Co-managed users?
While individual OUs can implement this for their units, Steve wanted to discuss whether or not there would be value in doing this for all Co-Managed units.
Wayne didn't like the idea because that would leave our machines vulnerable to internal attack from numerous unmanaged hosts. Then Steve inquired about doing this at the *.ifas.ufl.edu level. Wayne indicated that those records are not handed out to clients any more so that would be preferable but still perhaps unnecessary. He would prefer that we add individual entries as they were identified rather than using a wildcard entry.
Membership of ". IFAS-ICC" email distribution group to be narrowed to ICC members only
You are reminded that the ". IFAS-ICC" email distribution group does not include the broader audience which the ICC-L will reach. Plan your e-mails accordingly.
Wayne said that things he sends to ". IFAS-ICC" are meant for that narrower audience. Please don't reply to the ICC-L with such information, but keep it private to the narrower audience.
IFAS efforts toward Green IT (previous discussion)
Dan Cromer related that a "Green IT Taskforce" has been created and he is on that taskforce. One of their goals is to identify ways in which we can assist in saving energy. One of the approaches they intend to utilize is to hold a "town hall meeting" whose purpose would be to raise awareness. Dan wanted our input on whether we thought a physical meeting would be preferable to a "webinar" virtual meeting.
Dennis Brown mentioned a concern that negative feedback might get somewhat disruptive in an anonymous on-line setting unless there was some way to monitor and control input. Mitch Thompson suggested accepting questions in writing beforehand might be a solution there. Dan responded that having questions and concerns raised prior was a definite intention; they would try to then develop workarounds for any issues that might be raised.
Creating guest GatorLink accounts: singly or in bulk (prior discussion)
Steve had left this on the agenda in case further discussion was deemed warranted.
Can IFAS support DirectAccess in the future? (prior discussion)
Steve wants to keep this topic on our radar.
Moving away from the IFAS VPN service (previous discussion)
Steve assumes that moving our VPN to private IP is waiting on Wayne Hyde finding the time to implement.
VDI desktops as admin workstations (previous discussion)
This is another cool service that Wayne has in progress and which is awaiting sufficient time to pursue further.
Wayne's Power Tools (prior discussion)
Wayne has been working on a very cool tool which pulls data from multiple source to indicate various compliance issues with the machines within an OU. Wayne gave us all the heads-up a day prior to making this available:
|
Message to the ICC-L from Wayne Hyde: I am putting the final touches on a page that will combine various UFAD, Lansweeper, ePO and WSUS status on a single webpage. This will help OU admins determine whether their systems have the proper AV and Agent installed and if it is communicating with the various services. Warnings will be marked in yellow and errors in red. The page will also show computer naming issues and mark disabled as well as unused computer objects. Hopefully this will help in cleaning up our Active Directory. We currently have over 1500 disabled computer objects in IFAS that can be cleaned up. The Lansweeper database currently gets updated when a user logs on an IFAS machine, so information does get stale. Lansweeper scans can also be blocked by NAT or firewall issues. ePO and WSUS updates are agent driven and should be up to date unless the client is offline or not communicating properly due to a client-side error. For example, if you have been continually logged on your computer for 3 weeks and have not rebooted, your Lansweeper status may be 3 weeks old. WSUS and ePO should be current as long as the Agent and the Windows Update service is working properly. A sample row from the output is as follows: (click picture for large view) The column information is as follows: AD = UFAD computer object status. Disabled computer objects will have the usual red-X and a red cell background. Unused computer objects will have a yellow table cell background. If you hover the mouse over the computer graphic, you will get a tooltip showing the AD attributes “LastLogonTimestamp” and “LastPasswordSet” for the computer object. Computer = UFAD computer object name. If the computer does not conform to IFAS and UF computer naming standards the cell background will be yellow. This means the computer name must start with “IF” and also be 15 or fewer characters in length. (blank heading) LS/ePO/WU = used to show client status for the 3 databases. IP Address = Last known IP for the computer for each of the 3 services. This information is not always correct. User = Last known user according to LS and ePO. ePO Agent = ePO agent version according to LS and ePO. Out of date agents will have a yellow cell background. No agent installed will be red. There are cases when LS will report an agent and ePO will not – one is a computer that only has McAfee installed (VSE installs the agent in unmanaged mode and it does not check in with our ePO server). Another possibility is a computer that has an old agent still connecting to the OLD (very old) ePO server. Antivirus = VSE version installed according to LS and ePO. Out of date = yellow. None installed = red. ePO appends a minor version and ‘.Wrk’ or ‘.Srv’ to the version depending on the type of OS installed. Last Update = Last time the computer has been scanned by Lansweeper; last time the agents have checked in with ePO and WSUS. # Days = Number of days passed since the last scan or agent check-in. Last Reboot = Date of last reboot according to WSUS. IE Version = Internet Explorer version reported by Lansweeper scans. This information may be missing or out of date depending on the last LS scan. I didn’t configure LS to check for the registry key until last week, so many computers do not have this information stored in our database. There will be totals at the bottom of the page for total # of computer objects, # of disabled objects, # of unused objects, etc. I am working on detection of SusClientId conflicts. These conflicts are due to computers being deployed from a master image via ghost or some other duplication software where the registry keys were not deleted before shutting down and creating the master image. The current WSUS agent attempts to detect these conflicts and generate new SusClientId GUIDs, but it does not always work when computers are nearly identical in hardware configurations. Conflicts cause WSUS reporting to be inaccurate. For example, 30 computers may have the same SusClientId and similar hardware so the client agent does not regenerate the id. WSUS reporting will only show the last computer that checked in with that SusClientId making it impossible to know which clients have update errors, etc. More soon… |
The next day Wayne made it available, via the following notice:
|
Message to the ICC-L from Wayne Hyde: The new WPT is ready for folks to start using. It may be a bit slow right now due to some un-optimized SQL queries and other back-end factors (I yanked a drive on the SAN to test/time a rebuild on the new DAE for the file cluster). If you do get a query error, click submit again and it should go through. I tweaked the display a bit, so a sample good and bad table row now look like: (click picture for large view) You can read the WPT instructions/documentation on the first page. Log in and click “OU Computer Status” on the left: https://itsa.ifas.ufl.edu/ouadmin Direct link: https://itsa.ifas.ufl.edu/ouadmin/oucompstatus.asp At the bottom you will find how long the SQL query took to process and some OU totals. For example: SQL query time : 8 second(s) 10 : Total number of computer object(s) |
Steve pulled up this new tool and Wayne discussed various aspects of what this provides--most of which was covered in his prior e-mails as shown above.
Wayne mentioned that currently within IFAS that are 1,459 disabled computers; this amounts to 26% of our computer objects. Only 244 of those have been disabled less than six months. 426 computer objects were disabled between six month and one year ago and 601 were disabled between one and two years ago. There are even 188 computer objects that were disabled over two years ago! Some clean-up is obviously needed.
Wayne pointed out that there are also 165 misnamed computer object within IFAS. Names must begin with "IF" and be no longer than 15 characters in order to be compliant with policy.
Wayne explained that LanSweeper (LS) utilizes server-side polling and firewall and NAT issues will block it. There are circumstances where the LS data will not be up-to-date, which is why he displays the # of days since the last update. ePO, on the other hand uses an agent on the client-side and will not be blocked by a firewall. The "Last Reboot" column is as was reported by WSUS.
The IE version column comes from LS as well and may be out-of-date; LS only scans for software every one or two days so this last field may not be reporting correctly even if the computer was scanned today. Across IFAS we have 1045 computers with IE8, 1300 with IE7 and 69 with IE6. 1300 machines are listed as "unknown", which mean LS doesn't know about it yet.
OU Admins must install the agent and VSE
Dennis asked why VSE is no longer installed automatically. Wayne explained that this had to do with problems in using embedded credentials which had been used prior to allow those running w/o local admin rights to install it.
The best and surest method of install is to do it manually when you set up a machine. Alternatively, you can use the ePO console to tag a machine with the "PushCMA" tag. The problem with that latter method is that a firewall or NAT can block the installation; this is fairly common and in such situations you need to visit the machine and manually install. Once the agent is on the machine, however, the PushAV tag should work to deploy the antivirus software itself.
Kevin Hill asked about the various tags and Wayne responded that there are really only three tags which are meant for general use: PushCMA (for installing the agent), PushAV (for installing VSE), and PushAS (for installing the antispyware module). If tags are set for machines on which the corresponding items are already installed the tags are automatically cleared and do not remain. PushAV and PushAS are client side tasks and will not work unless the agent is already installed.
You may monitor the agent on the machine itself by viewing the Agent Activity Log. You can do this for a remote machine via "http://if-computername:8081/", where computername is the actual name of the machine being polled. You can also view the McAfee Agent Monitor on the local machine by right-clicking on the McAfee shield icon in the system tray and selecting that option:
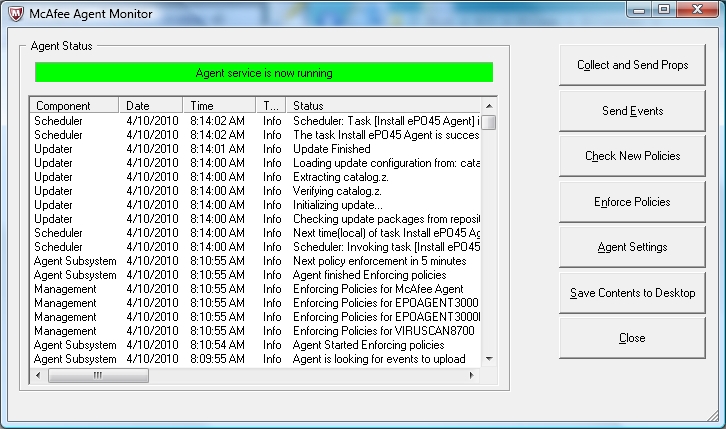
Kevin reported seeing McShield scan timeouts during which CPU usage spikes; users were experiencing temporary lockups as a result. Wayne asked Kevin to get with him about which machines were involved so he could assist in finding a cause/solution.
Steve mentioned that he had a few machines on which the agent was installed but communication wasn't working with the server. The solution there was to uninstall and reinstall the agent. Wayne noted that if the "OU Computer Status" WPT indicates that a particular machine has updated recently with LS but not ePO, then the agent is obviously not communicating.
Wayne noted that LS runs only on login and even then certain aspects of a machine's configuration are not noted at every run. Thus, it is not unusual to have any of the LS-reported data be out-of-date.
Wayne also noted that a standalone installation of VSE does install an unmanaged agent. Consequently, you will see machines for which the LS data lists an agent version (in yellow) but the ePO data is empty (red). This means the machine is not being managed and that the agent needs to be installed.
Winnie Lante asked about how it would be best to retain information of disabled machines so they could be removed from UFAD but be reincarnated fairly easily. Wayne suggested keeping that info in a spreadsheet. Even though such machines often turn up again and can be simply re-enabled to get them working again, actually deleting those objects is the only way to really clean up things. Perhaps we all should consider biting the bullet and doing this rather than waiting for Andrew to have the time to implement his previously discussed plan.
OU Technical Contact email groups being created
Wayne pointed out that distribution groups are being created to enable mailing OUAdmins for various purposes. That includes the planned automatic FSR reports concerning file server space usage (duplicate/large files/etc.).
Rapid security response is needed
Wayne also intends to rework the UFirt alerts so those can go only to the pertinent people. He expressed the importance of containing problem machines within 24 hours by taking such machines off-line ASAP while resolving the issue.
Wayne can use DHCP filtering for campus machines; this is a feature of W2k8 R2 Server. He can drop the MAC address into a filter list and that machine will not get an IP address. We will have that capability before too long with the remote sites as well since the new MPS servers are just beginning to roll out. Wayne can still do something similar via DHCP reservation at the remote sites, but a complicating issue is that many remote sites have long lease times--up to two weeks. That means any DHCP settings could take a long time to be effective. Also, setting a reservation entry for blocking ties up an IP.
Pushing Silverlight?
Wayne asked if people would object to him pushing Silverlight via WSUS. He would like to do that because not enabling that causes a status warning for each and every machine that does not have Silverlight installed. This messes up his status view within WSUS and makes it much harder to track overall machine status. Nobody seemed to object to Wayne doing that.
Beta-testing of computer compliance tool for potential use in login script
Chris Leopold is developing a tool for testing computer policy compliance which may be added to our login script at some point. He announced this via e-mail:
|
Message to the ICC-L from Chris Leopold: Program Announcement for IFAS Beta testers Name: procschk.exe Language: C# Location: "\\ad.ufl.edu\NETLOGON\IFAS\" Usage: "\\ad.ufl.edu\NETLOGON\IFAS\procschk if http://wsus3 /s" Issues:None Reported Why was this application: This application is to be used as a “last resort” catch-all to encourage users to report, or silently collect, UFAD and IFAS policy compliance issues to OU administrators with their machines. What does it do? After a cleanup effort is made to bring IFAS devices into compliance with UFAD and IFAS policy, this application *may* be placed in the \\ad.ufl.edu\netlogon\ifas\Login Script.vbs script. It currently checks your machine for the following UFAD and IFAS required policies. Is McAfee VirusScan installed and running on your machine? We can all agree that the above are small but important policies. This application has two modes of operation; “Interactive” and “Silent”. If it is run without the “/s” silent option *and* your system is out of compliance , the application will present the user with a message box detailing the issue(s) that were found. As an example:
(complete with spelling errors - you gotta love it) If this application is run in silent mode *and* your system is found to be non-complaint, it will “silently” collect and report all policy issues to a server on campus. If the policy issues with your machine are addressed (after being found non-compliant), the associated log file will be deleted on the campus server by the application. <- (look ma, it cleans up after itself!) Changes: I have made some modifications to what is being logged with the “/s”, silent option. Below is what is currently being written in to log files. >>--Begin Log File Sample--<< What is being asked of me? I am requesting that you help beta test this application by running it on a few machines within your OU. Additionally, I would like for you to use the silent mode option, i.e., specify the “/s” option. The application does a good job at letting you know that it did something by displaying action-related console messages, e.g., “Text Appended Successfully”, “File Created Successfully” and “File Deleted Successfully”. Remember, the application will *only* create a file if a problem was found *and* the user had specified the “/s” option. Make sure you pass a “bogus” arguments to the application to trigger a false positive. For example: Open a command prompt and type… Correct arguments should be: Next Try “bogus” false positive arguments that would be: Next Run the command using the correct arguments and you should see “File Deleted Successfully” Anything different? Run the command again without the “/s” option and see what is out of compliance with your system. Thanks |
Chris continued to work on the application in response to feedback and late Friday [!] he posted the following update"
|
Message to the ICC-L from Chris Leopold: All, I have completed a total re-write of procschk.exe based on some user feedback. In this version, the application uses an .xml file to import the values for the variables that it uses. IFAS Policy Compliance Checker Beta1 Example: Path to file location: \\ad.ufl.edu\netlogon\ifas\procschk Example of .xml file:
<?xml version="1.0" ?>:
- <Data>
- <Variables>:
<Variable Name="logPath" Value=
"\\IF-SRV-CRLE.AD.UFL.EDU\AppShareTest\" />:
<Variable Name="hisPath" Value=
"\\IF-SRV-CRLE.AD.UFL.EDU\AppShareTest\" />:
<Variable Name="vseProcess" Value="McShield" />:
<Variable Name="cmaProcess" Value="mcafeeframework" />:
<Variable Name="wsusRegPath" Value=
"SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate" />:
<Variable Name="wsusRegKey" Value="WUServer" />:
<Variable Name="wsusServer" Value=
"http://wsus3.ifas.ufl.edu" />:
<Variable Name="hostPrefix" Value="if" />:
</Variables>:
</Data>:
|
Using an XML configuration file makes the program more flexible as editing that file permits changing the way the program functions w/o the need to recompile.
Chris continues to tweak the application. He added a variable named "ldapDomain" to the .xml file and created a method named "GetDistinguishedName". The program will now do a LDAP lookup on the computer object, extract the OU name, and prefix it to the log file name. By doing this, Chris can enumerate the file names in the log directory (of machines that do not follow IFAS Policy) and email the computer names to a mail-enabled group that contain the local OU administrators.
With further refinements, Chris now has the program create folders for each OU and the program is writing the log files to the appropriate subfolder. Once a machine is fixed, at the next run the program will delete the associated log file and add an entry into the history.txt file at \\ad.ufl.edu\netlogon\ifas. This will maintain a list of machines that had problems that were later resolved. That OU subfolder structure and appropriate permissioning will permit controlling read access so that each OU Admin may see only their own log files. Furthermore, Chris has developed a server-side component which will run as a scheduled task which will look through the folders and e-mail the appropriate OUAdmins (using the groups discussed prior).
Finally, Chris has renamed the program file and its XML file to IPCC.EXE and IPCC.XML respectively (IPCC stands for "IFAS Policy Configuration Checker"). Chris did a quick demo of the program and how it could work then solicited comments on what ICCers thought of it and what timeframe might possibly be put to its installation in the login script.
Discussion
Dennis asked if the security groups being used for notification could have multiple individuals so that if he was out someone else could get those. Chris responded that this was indeed the case. Dennis then added that he liked the silent mode operation because having these pop-up on the user's workstation would make him a little nervous.
Wayne pointed out that after an issue was fixed, running Chris's routine manually (via "\\ad.ufl.edu\netlogon\ifas\ipcc.exe \\ad.ufl.edu\netlogon\ifas\ipcc.xml") should be part of our standard remedial procedures. Otherwise, the log files will remain until the next logon and be out-of-sync with the true status.
Winnie said that she has quite a problem with machines out at Fisheries. She knows many are non-compliant but has no information on the machines at all since the computer accounts were not documented within the description field. She would appreciate running this in non-silent mode to see if that might prompt the cooperation of the users of those machines. She has sent out general e-mails in attempts to locate these but has gotten no response. Wayne pointed out that the program run entry could be placed into each "_IFAS-OU-USERS_autoGS" script and then the OUAdmins could decide whether it should run silently or not.
Steve mentioned that he would be happy if the server-side component ran constantly as a service rather than as a scheduled task. That modification could permit nearly immediate e-mail notification when someone plugged in a non-compliant machine and logged on.
It looks like we have a GO!
There seemed to be no complaint from the ICC membership with implementing this soon. Chris agreed to put the finishing touches on the program as soon as is feasible and then to send out notification prior to implementation. Documentation on understanding these notices and on how to remediate the various potential compliance issues is planned as well.
Folder permissioning on the IFAS file server
You are reminded to please take the time to read and implement the new standards. If you have any questions get with Wayne or Steve.
Disabling/deleting computer accounts based on computer password age
This is yet another matter for which finding time for implementation is proving difficult. Steve wants folks to remember that Andrew has a good plan for dealing with this which he simply has had no time to address. In the meantime, it would be very good of each OUAdmin to consider mimicking the proposed plan manually by keeping their own records and deleting any computer object which have been disabled for 90 or more days; Wayne's Power Tools can identify those. Steve has finally begun doing that for his own unit and it has made his view within ADUC much more agreeable.
Andrew reported that the new MPC was fully functional at Fisheries now. When asked how difficult the transition was, Andrew replied that it went pretty well thanks to help from Winnie. This first rollout has been a very useful learning experience and we now should be much better prepared to proceed with other locations soon.
Updating our virtual infrastructure software
It was reported last meeting that Wayne has us upgraded now to VSphere 4. As might be expected, there are a number of new features.
SAN upgrade status
Wayne reported that the new DAE has been added to the SAN now and the long process of consolidating has begun. Twelve to fourteen 2TB LUNs will be moved to four 8TB and two 4TB LUNs on the file server. A number of departments will then be collapsed onto a single large drive instead of maintaining a bunch of small drives. Those migration steps which are transparent to the users have already been accomplished.
The next step for each department will be to robocopy the data from the old drive to the new one. [Wayne reported Saturday that it took 20 hours to copy the WEC data, though that was while backups were going on. 150,315 folders and 1,788,130 files for an overall rate of 26MB/s. Lots of small files make for slow going.] Then Wayne will use Beyond Compare from Scooter Software to assure everything is identical. The final step will involve a small "outage" where the unit will have read-only access; that will permit a final robocopy and integrity check before pointing DFS to the new location.
Other than the previous discussions regarding the new WPT and the proposed IFAS Policy Compliance Checker implementation there was nothing to report.
Status of SharePoint services (prior discussion)
IFAS migrating to centralized MOSS
There was no news to report this month.
Public folder file deletion policies and procedures status
Nothing further was available on this topic at this time.
Microsoft
There was an out-of-band (OOB) security update for IE in late March. [Podcast - Security Bulletins for the regular IT guy"] Wayne noted that WSUS is set to approve OOB patches for all clients as soon as they are received; so as soon as they appear our machines will begin updating.
The April Microsoft patches will include six "important" and five "critical" bulletins.
Adobe
Adobe posted a "blog entry offering guidance for launch functionality mitigation in Acrobat and Reader. They will also be rolling out Adobe Reader and Acrobat 9.3.2 and 8.2.2 updates next Tuesday.
Java
Java Version 6 release 19 (1.6.0_19) is now available; this is a security update. The current security baselines for various versions is available here
QuickTime
A QuickTime update to version 7.6.6 is now available.
Other recently available security updates include:
MS Office News update
Steve had no news to relate this month.
Job Matrix Update status
This is here as a standing topic--no discussion this month.
Remedy system status (previous discussion)
Steve asked again if anyone had any issues with using the new system.
Was there an edict back around the late 1990s that AOL was not to be installed on any UF machine?
Fergie raised this question. He seems to remember some such thing but has not been able to discover any collaboration of that. Chris Leopold mentioned there were many problems with AOL being blocked for e-mail and Steve remembered grumbling about how aggressive that software was in modifying the network stack, but nobody could recall something along the lines of what Fergie was suggesting. If anyone knows or finds any information on this he would appreciate you contacting him.
ITSA staff down to one next week
Chris Leopold wanted everyone to realize that Andrew, Santos and himself would be out next week due to "The Windows in Higher Education Conference 2010". Consequently, Wayne will be left holding the boat. Please bear with him and try to avoid interrupting him unnecessarily during this time.
PDF-Xchange (prior discussion)
Steve wants to keep this on our agenda for possible latter consideration and noted that Micah Bolen has been using this product for his units.
Interest in Wordpress blog systems, and photo gallery systems that require PHP and MySQL
Due to running late we did not have time to consider this topic this month.
The meeting was adjourned a bit late at about 12:10 PM